- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiAP
- FortiClient
- FortiADC
- FortiAnalyzer
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiExtender
- FortiEDR
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiWebCloud
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- HTTPS Forwarding not working correctly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS Forwarding not working correctly
Hi all,
Running v6.2 firmware and not able to perform a simple port forward to an HTTPS server internally, something odd in the Fortinet logic or is it a known issue?
Trying to access an internal HTTPS server from outside, I've setup a NAT (Virtual IP) for the external IP, internal IP of the web server and using port 445 on the outside and 443 inside. Added the corresponding IPv4 policy to allow HTTPS traffic through.
When browsing the external IP on https://x.x.x.x:445 i'm receiving the Fortigate login page rather than the expected internal web server. The NAT doesn't appear to be working as it should, what's wrong with the above config?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Trying to access an internal HTTPS server from outside, I've setup a NAT (Virtual IP) for the external IP, internal IP of the web server and using port 445 on the outside and 443 inside. Added the corresponding IPv4 policy to allow HTTPS traffic through.
and
When browsing the external IP on https://x.x.x.x:445
We would have to see your DNAT VIP and FWpolicy, Every thing else mention and about service ports should not be applicable here not anything else stated unless you change the admin.port of the firewall to 445
Fwiw; tcp.port 445 is NOT an admin-port for any Fortigate. You can quickly determine this by looking at your config sys global and check if you have SET tcp.port 445 for admin. if you have than Dave and others already gave you the reason and the fix.
Ken Felix
PCNSE
NSE
StrongSwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm well aware that 445 is not used by Fortigate hence the reason to select it. It is however used internally on 443 and I suspect it's not able to NAT correctly internally to a different IP when using 443.
David provided a workaround, this is not a fix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No your still confused, Dave provide you the fix & not a work around. You are not listening to the wise information given to you.
You need to show you config and determine if you admin port is 445. It seems like it is. As far as NAT the DNAT vip does that automatically so no need for nat in the fwpolicy.
Ken Felix
PCNSE
NSE
StrongSwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Site: https://tcpdump101.com
Twitter: https://twitter.com/Grave_Rose
Reddit: https://reddit.com/r/tcpdump101
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me spell out the difference for you.
Workaround: Changing internal web server port to allow access remotely OR changing SSLVPN/Admin port on Fortigate
Fix: Fortigate allows port 445 (any free external port) externally on it's own IP to an internal web server IP on 443 (HTTPS).
Rather than become obnoxious, read the facts in my post. Admin port is not running on 445.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Grave_Rose. Yes had already tried that for the rule related to that traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Site: https://tcpdump101.com
Twitter: https://twitter.com/Grave_Rose
Reddit: https://reddit.com/r/tcpdump101
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh, one other thing to check... When you set up the VIP, did you specify that it was PAT and not NAT? On mobile right now so I can't check but I believe the option is just called "Port Forwarding" in the VIP object.
*Edit
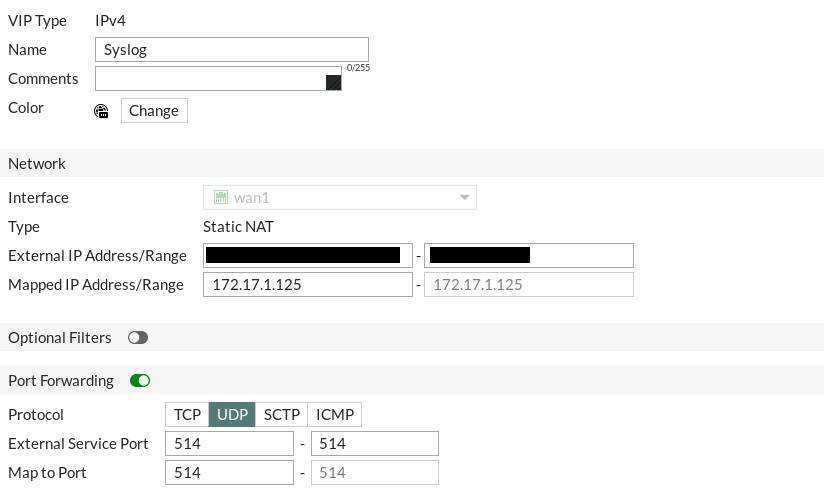
So I'm back in front of a box and the clue to this was when you said "it's own IP" which meant that you're doing Static PAT and not Static NAT as I (as well as others probably) assumed. This is why it seemed so strange, at least to me. :) I've got the same thing configured at home with my 'Gate but for remote syslog. I was going to attach both screenshots but apparently I can only attach one file so I've added a screenshot of my VIP object. Just use this object in your policy (make sure NAT is disabled) and you should be good to go. Set the "External Services Port" to 445 and the "Map to Port" as 443. Bingo-bango-bongo you're all set. Hope this helps.
Sean (Gr@ve_Rose)
Site: https://tcpdump101.com
Twitter: https://twitter.com/Grave_Rose
Reddit: https://reddit.com/r/tcpdump101
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes this was already done in the original post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hrm... Okay. Without your config, I've got one last idea. Run the following commands. Replace 1.2.3.4 with an external host that you can test with which you will only use for this test - We don't want to capture any traffic which isn't destined for your public IP address on TCP/445. Make sure you have your SSH session logging output or have a large enough scroll-back buffer since this will generate a lot of information:
diagnose debug disable diagnose debug flow trace stop diagnose debug flow filter clear diagnose debug reset diagnose debug flow show function-name enable diagnose debug flow show iprope enable diagnose debug flow filter addr 1.2.3.4 diagnose debug flow trace start 5 diagnose debug enable
With this running, connect to hxxps://y.y.y.y:445 from 1.2.3.4 and it should load up the login page as it has been already. You should have a lot of information in the deubgs on your SSH session. Stop the debug with:
diagnose debug disable
If you can, post the output of that to the thread and we can see what's happening on the firewall from an internal processing view.
Sean (Gr@ve_Rose)
Site: https://tcpdump101.com
Twitter: https://twitter.com/Grave_Rose
Reddit: https://reddit.com/r/tcpdump101
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- Need Help with Configuring SNMP for... 110 Views
- Help Needed: DDNS Not Working and... 469 Views
- Setting up Forticlient on an Ipad 365 Views
- RSSO issue 131 Views
- VIP Port Forwarding Settings for Mapping... 305 Views
-
FortiGate
7,037 -
FortiClient
1,389 -
5.2
801 -
5.4
639 -
FortiManager
610 -
FortiAnalyzer
446 -
6.0
416 -
FortiAP
369 -
FortiSwitch
368 -
5.6
362 -
FortiClient EMS
286 -
FortiMail
272 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
172 -
6.4
128 -
FortiNAC
123 -
FortiGuard
112 -
IPsec
104 -
SSL-VPN
94 -
FortiGateCloud
93 -
FortiSIEM
92 -
FortiCloud Products
88 -
FortiToken
76 -
Customer Service
71 -
Wireless Controller
64 -
4.0MR3
64 -
FortiProxy
48 -
FortiADC
45 -
Fortivoice
44 -
SD-WAN
43 -
FortiEDR
42 -
FortiDNS
37 -
FortiExtender
36 -
FortiGate v5.4
35 -
FortiSandbox
33 -
FortiAuthenticator
32 -
FortiSwitch v6.4
32 -
Firewall policy
32 -
VLAN
28 -
High Availability
28 -
FortiConnect
24 -
FortiWAN
23 -
ZTNA
21 -
DNS
21 -
FortiConverter
21 -
BGP
19 -
FortiGate v5.2
19 -
Certificate
19 -
SAML
18 -
FortiPortal
18 -
FortiSwitch v6.2
17 -
LDAP
17 -
VDOM
16 -
FortiMonitor
14 -
Authentication
14 -
FortiLink
14 -
Interface
14 -
FortiDDoS
14 -
Logging
14 -
FortiGate v5.0
13 -
Fortigate Cloud
13 -
Routing
13 -
FortiCASB
12 -
RADIUS
11 -
NAT
11 -
Web profile
11 -
SSL SSH inspection
10 -
Traffic shaping
10 -
Virtual IP
10 -
SSO
10 -
Application control
10 -
FortiRecorder
10 -
SSID
9 -
FortiWeb v5.0
9 -
FortiManager v5.0
9 -
4.0MR2
9 -
IP address management - IPAM
8 -
FortiBridge
8 -
WAN optimization
8 -
FortiGate v4.0 MR3
8 -
RMA Information and Announcements
7 -
FortiSOAR
7 -
FortiAnalyzer v5.0
7 -
SNMP
7 -
Web application firewall profile
7 -
Admin
7 -
4.0
7 -
Proxy policy
6 -
Security profile
6 -
Traffic shaping policy
6 -
Static route
6 -
FortiDirector
5 -
IPS signature
5 -
Packet capture
5 -
FortiAP profile
5 -
Automation
5 -
FortiManager v4.0
5 -
FortiDeceptor
4 -
Antivirus profile
4 -
DNS Filter
4 -
FortiTester
4 -
FortiCarrier
4 -
FortiCache
4 -
OSPF
4 -
Web rating
4 -
3.6
4 -
FortiScan
4 -
trunk
4 -
Port policy
4 -
System settings
3 -
Fortinet Engage Partner Program
3 -
FortiToken Cloud
3 -
Traffic shaping profile
3 -
FortiPAM
3 -
DoS policy
3 -
Email filter profile
3 -
FortiDB
3 -
Intrusion prevention
3 -
Protocol option
2 -
FortiInsight
2 -
NAC policy
2 -
Users
2 -
FortiAI
2 -
Application signature
2 -
VoIP profile
2 -
FortiHypervisor
2 -
Fabric connector
2 -
Netflow
2 -
Multicast routing
2 -
4.0MR1
1 -
TACACS
1 -
Subscription Renewal Policy
1 -
Replacement messages
1 -
FortiCWP
1 -
FortiNDR
1 -
Schedule
1 -
SDN connector
1 -
Authentication rule and scheme
1 -
FortiManager-VM
1 -
DLP sensor
1 -
Internet Service Database
1 -
Explicit proxy
1 -
Zone
1
| User | Count |
|---|---|
| 1041 | |
| 862 | |
| 512 | |
| 441 | |
| 146 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.