- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Support Forum
- I can't connect HP vlan to Fortigate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't connect HP vlan to Fortigate
Hello
i have fortigate 80c and hp switch 1910.
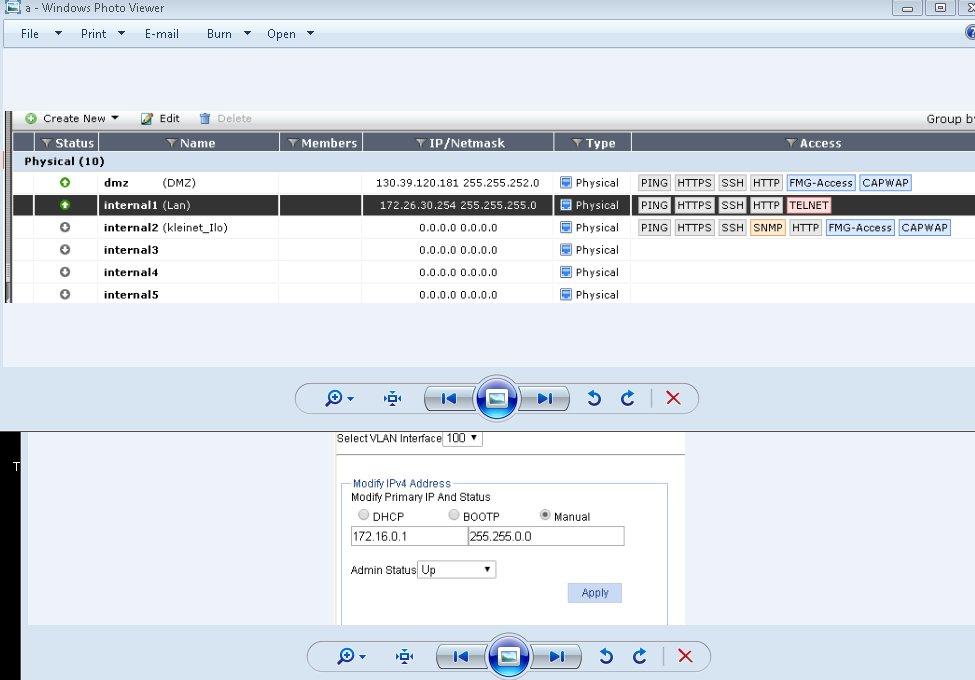
my network (internal 1 ) working with 172.26.30.254/255.255.255.0.
now i created on hp switch vlan 100 with interface 172.26.0.1/255.255.0.0.
how can i connect vlan 100 to my fortigate ?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to select that port that you have connected to the switch (under network interfaces) then click "new" and go to vlan.
The Gate won't listen to a vlan using just the port being connected unless it is the default vlan of the switch. Since 100 isn't, you need to have a vlan100 configured on the physical interface of the Gate as well (which means you will get a drop down on internal1 for vlan100).
Mike Pruett
- « Previous
- Next »
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Current setup is HA enviroment whereby Hp port 23 = FortiGate (Master) port 1 and Hp port 24 = FortiGate (Slave) port 1.
I have tried only tagged vlan for trunk port 23 & 24 and untagg for the remaining based on vlan assignment e.g 1-18 vlan 10. plug my notebooked and set the IP and gateway same as vlan 10 subnet and encounter same issue unable to reach fortiGate unless the port is configured as tagged. Do i need to check anything on FortiGate since inter vlan policy communication is handle by zone?.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@azwanarif
You should not put port 23+24 into an HP Trunk.
HP Trunking is only for load balancing multiple connections from one HP switch to one Fortigate.
In Fortigate this is called an aggregated interface.
This is used for increase of bandwidth between switches and Fortigates.
Fortigate supports using aggregated LACP on specific models, but yours does not.
You are using an HA setup, which splits the connections over two (or more) single fortigates.
This is a redundant interface, not a aggregated interface, huge difference 
In a Fortigate HA setup the units are not stacked, they operate as separate nodes beeing controlled by the master.
All redundant interfaces within an Fortigate HA setup operate individually and do not require usage of HP trunking.
In all HA setups control information is send over the HA link between the nodes using FGCP.
If you are using an active-active setup , actual traffic between the nodes can be send over the HA link(s).
Your setup will actually drop traffic initiated to the second fortigate as initated traffic always goes to the primary fortigate. In active-passive or vdom clustering mode traffic will be fully processed by the primary unit, in active-active mode the primary might send the request over to the secondary unit to process the traffic.
But there are several caveats in that.
For further details I will refer to the Fortigate 6.0.5 handbook regarding HA:
https://docs.fortinet.com/document/fortigate/6.0.5/handbook/643919/high-availability
You did not mention where the other ports are connected to.
Fortigate A port1 is connected to port23 on the HP switch, which is part of the Trk interface.
In your HP switch configuration you now have placed all vlans on this Trk interface.
VLAN1 is untagged, VLAN 10 and VLAN102 are tagged.
Looking from the Fortigate perspective this is good. Keep it like this on the Fortigate side.
Hardware switch "lan" will receive and send traffic untagged and the HP switch places this traffic in VLAN1.
Hardware switch "lan" sub/vlan interface X will receive and send traffic tagged with vlan X and the HP switch places this traffic in vlan X.
You should put the other vlans you have on the HP switch with tagged port 23 and tagged port 24 (remember no Trunk)
Fortigate port 2 should NOT be connected to the same switch or the same network. You can connect this port to an endpoint (client or server), but it should not make a loop in the network.
For the HP switch perspective you should remove the Trk interface and put the vlans on both port 23 and port 24.
On port 23 and port 24 vlan1 untagged, the rest tagged.
For your client ports it depends if that traffic is processed untagged or tagged.
If your clients , like iDRAC, are set up to use a vlan than this is tagged.
If your clients , like your laptop without additional configuration, are set up without a vlan this is untagged.
Try this, place a client port on the HP switch (1-18) of vlan 10 in untagged mode, connect your laptop without specifying a vlan and you will get connection to the fortgate interface in vlan 10.
Regarding zones:
If you place multiple interfaces (aka members) into a zone, this can simplify policy rules.
A policy rule can only be created from/to the zone, not the individual members.
For a zone it is possible to allow intra-zone communication with a setting in the zone configuration.
This is the same as making a policy from source interface zone , destination zone, source all, destination all, service all, no nat. Basically an ANY-ANY rule for all members in the zone.
The checkmark you can setup in the zone configuration BLOCKS the intrazone communication.
All traffic between the members will now be denied except for traffic specifically mentioned in a firewall policy.
This is how you mentioned your current setup:
" Hp switch is connected directly to Fortigate port 1 (Hardware switch) and using Zone to combine all VLAN with "Block intra-zone traffic" disable to reduce multi policy between Vlan."
Yes, this will block all traffic between the members in the zone.
Remember the default behaviour in a fortigate for interfaces that are not in the same zone is block.
For example traffic between the zone and "lan" is blocked by default.
If you would remove all the vlan interfaces from the zone, all will still be blocked by default and you would need to create policies to allow traffic between these interface.
This allows for more control on the traffic between the members, but off course increased the amount of policies in the policy view.
Tip, you can change the system>features to allow for a policy from and to multiple interfaces, reducing the amount of policies that do the same.
Note, this will change the interface view to section view only.
You could make a policy from all the vlan interfaces to all the vlan interfaces allowing all without NAT, which does the same thing as the zone with the allow of intra-zone traffic, your choice.
TLDR :
Remove HP Trunk
Put vlan1 untagged on port 23 and port 24 , other vlans tagged on port 23 and port 24
Don't connect Fortigate port2 to the same network
Check HA setup and behaviour
Check zone setup and behaviour
((wow this was a long one, usually I get payed for this ;p , but for you it's completely free ))
Consultant @ Exclusive Networks BV
Datacenter Networking and Security
FCSS EFW/SDWAN
Fortinet, HPe/Aruba, Arista, Juniper and many more
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dennisv wrote:@azwanarif
You should not put port 23+24 into an HP Trunk.
HP Trunking is only for load balancing multiple connections from one HP switch to one Fortigate.
In Fortigate this is called an aggregated interface.
This is used for increase of bandwidth between switches and Fortigates.
Fortigate supports using aggregated LACP on specific models, but yours does not.
You are using an HA setup, which splits the connections over two (or more) single fortigates.
This is a redundant interface, not a aggregated interface, huge difference
In a Fortigate HA setup the units are not stacked, they operate as separate nodes beeing controlled by the master.
All redundant interfaces within an Fortigate HA setup operate individually and do not require usage of HP trunking.
In all HA setups control information is send over the HA link between the nodes using FGCP.
If you are using an active-active setup , actual traffic between the nodes can be send over the HA link(s).
Your setup will actually drop traffic initiated to the second fortigate as initated traffic always goes to the primary fortigate. In active-passive or vdom clustering mode traffic will be fully processed by the primary unit, in active-active mode the primary might send the request over to the secondary unit to process the traffic.
But there are several caveats in that.
For further details I will refer to the Fortigate 6.0.5 handbook regarding HA:
https://docs.fortinet.com/document/fortigate/6.0.5/handbook/643919/high-availability
You did not mention where the other ports are connected to.
Fortigate A port1 is connected to port23 on the HP switch, which is part of the Trk interface.
In your HP switch configuration you now have placed all vlans on this Trk interface.
VLAN1 is untagged, VLAN 10 and VLAN102 are tagged.
Looking from the Fortigate perspective this is good. Keep it like this on the Fortigate side.
Hardware switch "lan" will receive and send traffic untagged and the HP switch places this traffic in VLAN1.
Hardware switch "lan" sub/vlan interface X will receive and send traffic tagged with vlan X and the HP switch places this traffic in vlan X.
You should put the other vlans you have on the HP switch with tagged port 23 and tagged port 24 (remember no Trunk)
Fortigate port 2 should NOT be connected to the same switch or the same network. You can connect this port to an endpoint (client or server), but it should not make a loop in the network.
For the HP switch perspective you should remove the Trk interface and put the vlans on both port 23 and port 24.
On port 23 and port 24 vlan1 untagged, the rest tagged.
For your client ports it depends if that traffic is processed untagged or tagged.
If your clients , like iDRAC, are set up to use a vlan than this is tagged.
If your clients , like your laptop without additional configuration, are set up without a vlan this is untagged.
Try this, place a client port on the HP switch (1-18) of vlan 10 in untagged mode, connect your laptop without specifying a vlan and you will get connection to the fortgate interface in vlan 10.
Regarding zones:
If you place multiple interfaces (aka members) into a zone, this can simplify policy rules.
A policy rule can only be created from/to the zone, not the individual members.
For a zone it is possible to allow intra-zone communication with a setting in the zone configuration.
This is the same as making a policy from source interface zone , destination zone, source all, destination all, service all, no nat. Basically an ANY-ANY rule for all members in the zone.
The checkmark you can setup in the zone configuration BLOCKS the intrazone communication.
All traffic between the members will now be denied except for traffic specifically mentioned in a firewall policy.
This is how you mentioned your current setup:
" Hp switch is connected directly to Fortigate port 1 (Hardware switch) and using Zone to combine all VLAN with "Block intra-zone traffic" disable to reduce multi policy between Vlan."
Yes, this will block all traffic between the members in the zone.
Remember the default behaviour in a fortigate for interfaces that are not in the same zone is block.
For example traffic between the zone and "lan" is blocked by default.
If you would remove all the vlan interfaces from the zone, all will still be blocked by default and you would need to create policies to allow traffic between these interface.
This allows for more control on the traffic between the members, but off course increased the amount of policies in the policy view.
Tip, you can change the system>features to allow for a policy from and to multiple interfaces, reducing the amount of policies that do the same.
Note, this will change the interface view to section view only.
You could make a policy from all the vlan interfaces to all the vlan interfaces allowing all without NAT, which does the same thing as the zone with the allow of intra-zone traffic, your choice.
TLDR :
Remove HP Trunk
Put vlan1 untagged on port 23 and port 24 , other vlans tagged on port 23 and port 24
Don't connect Fortigate port2 to the same network
Check HA setup and behaviour
Check zone setup and behaviour
((wow this was a long one, usually I get payed for this ;p , but for you it's completely free ))
Hi @dennisv
Appreciate the advice ,
,
I have follow your guide on above post except for remove the port 24 on hp switch to secondary (Slave) FGT, currently i'm only able to do troubleshooting remotely due to site location required for traveling.
Based on screenshot below, I'm not sure because of the iDRAC 9 configuration all port at switch is required to be tagged (probably only HP switch), we already spoke with the server vendor and verified that only IP and gateway without vlan is configured.
We have 4 unit Dell EMC server which has been assigned IP 10.101.10.1-4. On my previous post port 1-18 is tagged with vlan 10 and only iDRAC with IP 10.101.10.3 is accessible with trunk enable, However once remove trunk with all port 1-18 is tagged all server is accessible except iDRAC IP 10.101.10.4 which possibly have issue with configuration.


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
azwanarif wrote:All access port: ports to PCs, printers, etc. should be untagged unless there is a specific reason to add the tag. This requires additional configuration on the workstation end. Your ports 1-18, and 19-20 are tagged in the configuration. That more than likely won't work unless there is a dumb device (Q-tag unaware switch/hub) in the middle that is dropping the tags.Thanks everyone for the info sharing,
Below is the current working HP Procurve configuration which required ethernet port to set as tagged for client vlan that connected to the HP switch to connect with gateway and other vlan beside than trunk port (Trk1) on 23-24.
I have tried with untagged port configuration the client is unreachable either from FortiGate or other vlan.
[attachImg]https://forum.fortinet.com/download.axd?file=0;176423&where=message&f=Switch.png[/attachImg]
Bob - self proclaimed posting junkie!
See my Fortigate related scripts at: http://fortigate.camerabob.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes this seems like a configuration issue on the iDRAC side.
You mentioned :
"we already spoke with the server vendor and verified that only IP and gateway without vlan is configured."
This implies the traffic from iDRAC to be untagged and HP port 1-18 should be set to untagged vlan 10.
But in a previous post you mentioned that iDRAC was setup with vlan 10 inside iDRAC, which implies HP port 1-18 should be set to tagged vlan 10.
Make sure you contact the server administrator and have them verify (screenshots) the proper iDRAC settings.
Anyway, you are on the right path now and it seems the connection between the HP switch and Fortigate is ok.
If you need any additional help with this connection, just reply to this thread and ill get a notification.
Consultant @ Exclusive Networks BV
Datacenter Networking and Security
FCSS EFW/SDWAN
Fortinet, HPe/Aruba, Arista, Juniper and many more
- « Previous
- Next »
-
FortiGate
11,006 -
FortiClient
2,254 -
FortiManager
926 -
FortiAnalyzer
703 -
5.2
687 -
5.4
638 -
FortiSwitch
608 -
FortiClient EMS
604 -
FortiAP
577 -
IPsec
472 -
6.0
416 -
SSL-VPN
405 -
FortiMail
387 -
5.6
362 -
FortiNAC
315 -
FortiWeb
266 -
6.2
251 -
FortiAuthenticator v5.5
234 -
SD-WAN
215 -
FortiAuthenticator
195 -
FortiGuard
164 -
FortiGate-VM
156 -
5.0
152 -
Firewall policy
152 -
6.4
128 -
FortiCloud Products
122 -
FortiSIEM
116 -
FortiToken
115 -
FortiGateCloud
113 -
Wireless Controller
97 -
High Availability
95 -
Customer Service
91 -
SAML
84 -
Routing
84 -
ZTNA
82 -
FortiProxy
81 -
Authentication
76 -
VLAN
76 -
BGP
75 -
Fortivoice
74 -
DNS
74 -
Certificate
74 -
FortiEDR
73 -
FortiADC
71 -
RADIUS
68 -
LDAP
66 -
FortiLink
62 -
SSO
61 -
NAT
58 -
FortiSandbox
57 -
Interface
54 -
FortiExtender
53 -
Application control
52 -
VDOM
50 -
4.0MR3
49 -
Virtual IP
48 -
Logging
44 -
FortiDNS
43 -
SSL SSH inspection
42 -
FortiPAM
41 -
Web profile
39 -
FortiGate v5.4
38 -
FortiSwitch v6.4
38 -
FortiConnect
36 -
Automation
36 -
FortiWAN
32 -
FortiConverter
31 -
API
30 -
Traffic shaping
29 -
FortiGate v5.2
28 -
FortiGate Cloud
27 -
Static route
27 -
SSID
26 -
SNMP
25 -
System settings
24 -
FortiSwitch v6.2
23 -
FortiPortal
23 -
OSPF
23 -
WAN optimization
22 -
Web application firewall profile
22 -
FortiMonitor
21 -
Web rating
20 -
IP address management - IPAM
20 -
FortiSOAR
19 -
Security profile
19 -
FortiAP profile
18 -
FortiGate v5.0
16 -
FortiDDoS
16 -
Explicit proxy
16 -
Admin
16 -
IPS signature
15 -
Traffic shaping policy
15 -
Proxy policy
15 -
Intrusion prevention
15 -
FortiManager v4.0
14 -
FortiCASB
14 -
NAC policy
14 -
Users
14 -
FortiManager v5.0
13 -
DNS filter
13 -
FortiDeceptor
12 -
Fabric connector
12 -
Port policy
12 -
FortiBridge
11 -
FortiRecorder
11 -
trunk
11 -
Traffic shaping profile
11 -
Authentication rule and scheme
11 -
FortiAnalyzer v5.0
10 -
FortiWeb v5.0
10 -
Fortinet Engage Partner Program
10 -
FortiGate v4.0 MR3
9 -
RMA Information and Announcements
9 -
Antivirus profile
9 -
Application signature
9 -
FortiCache
8 -
FortiToken Cloud
8 -
Packet capture
8 -
Vulnerability Management
8 -
4.0
7 -
4.0MR2
7 -
VoIP profile
7 -
FortiScan
6 -
FortiNDR
6 -
DoS policy
6 -
FortiCarrier
5 -
FortiTester
5 -
DLP profile
5 -
DLP sensor
5 -
Email filter profile
5 -
Protocol option
5 -
TACACS
5 -
Service
5 -
Cloud Management Security
5 -
3.6
4 -
FortiDirector
4 -
Internet service database
4 -
DLP Dictionary
4 -
Netflow
4 -
Replacement messages
4 -
SDN connector
4 -
Multicast routing
4 -
FortiDB
3 -
FortiHypervisor
3 -
FortiAI
3 -
Kerberos
3 -
Video Filter
3 -
File filter
3 -
Multicast policy
3 -
FortiEdge Cloud
3 -
FortiInsight
2 -
Schedule
2 -
ICAP profile
2 -
Zone
2 -
Lacework
2 -
FortiGuest
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Subscription Renewal Policy
1 -
FortiSASE
1 -
Virtual wire pair
1 -
FortiPresence
1 -
FortiEdge
1 -
FortiAIOps
1
| User | Count |
|---|---|
| 2841 | |
| 1436 | |
| 812 | |
| 802 | |
| 455 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2025 Fortinet, Inc. All Rights Reserved.