- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDDoS
- FortiDAST
- FortiDB
- FortiDNS
- FortiDevSec
- FortiDeceptor
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGuard
- FortiGate Cloud
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiToken
- FortiTester
- FortiWAN
- FortiVoice
- FortiWeb
- FortiWebCloud
- RMA Information and Announcements
- Wireless Controller
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- Re: Is there a work around for this type of SSL Er...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a work around for this type of SSL Error?
Hello,
We're running a Fortigate 500D firewall
Our users behind the firewall just suddenly started to see this message trying to access anything related to Google:
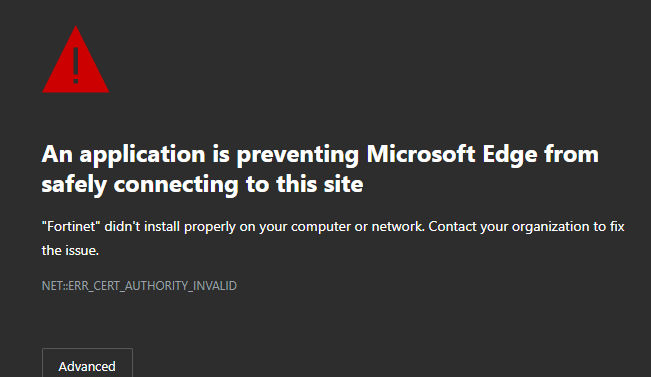
I checked our IPv4 policies, and anything from inside out the WAN has App, Web, and SSL profiles applied. I suspect the problem is with the SSL profile, but it doesn't let me disable it without disabling the APP and Web filter too.
Is there a way to disable the SSL profile from the CLI or another workaround? Or, even better, an actual solution for this problem?
Sadly I cannot call support because we don't have that lic.
- Labels:
-
Fortigate
Nominate a Forum Post for Knowledge Article Creation
Nominating a forum post submits a request to create a new Knowledge Article based on the forum post topic. Please ensure your nomination includes a solution within the reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You either have deep inspection turned on on the SSL profile. Check to make sure. You should be using certificate inspection only.
Now sometimes FGT will need to present a message even with just cert inspection and in this case will give you a cert warning because its not trusted from the FGT.
Can you show the config for your SSL Profile?
Graham
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm using the default "certificate-inspection"
It doesn't seem to be doing any deep-inspection, which is why this error is odd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It could be FortiGuard is unreachable to determine web rating and thus you are presented with an error (which can't be displayed because it's using untrusted FGT cert)
Graham
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi mksherman,
Could you check the certificate used by the browser when the issue happens. Also, please if the traffic is hitting the correct policy with certificate inspection or any other policy with deep inspection.
If you create a policy for a single user with no-inspection and access the site, is the still working without any cert errors?
Regards,
Vimala
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
You should put the Fortinet CA certificate in the end user machine's Trusted root CA directory, as this is necessary for the deep inspection to function properly.
In case if you dont want any SSL inspection you can disable it from the cli
# config firewall policy
# edit <policy id>
# set ssl-ssh-profile no-inspection
# end
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, can you clarify the syntax?
config firewall policy it goes to:
Is this where I put the number of the ipv4 policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The easiest way is on GUI to right-click the policy and say "edit in CLI".
You can also remove the inspection on the GUI however all the same. You must remove all security profiles, save, then open again and you can select no-inspection.
The error can be circumvented with the no-inspection, but it would be better to not work around a problem, but fix it.
- The browser shows the error as it doesn't trust the certificate.
- the certificate (of the web server that FortiGate shows) is not trusted because the browser doesn't have the web servers CA certificate included.
- The FortiGate replaces the original certificate because of a reason.
The reasons could be many:
a) FortiGate is trying to present a block page. Someone disallowed you to access the google-related pages.
b) FortiGate is protecting against a faulty certificate received from the other web server. Google usually would not have it, but another deep-inspecting node between FortiGate and Google might replace the certificate all the same with some certificate that FortiGate doesn't trust.
c) FortiGate is set up for deep inspection somewhere (as you said that is not the case)
There might be more and I forgot.
In either of these cases:
FortiGate has to block HTTPS access from client to server and requires breaking TLS with a man-in-the-middle-attack. It needs to re-sign the connection with its own web server certificate, signed by a CA certificate present on FortiGate. Clients by default do not trust it.
In case b) the FortiGate will use the "untrusted CA", in case a) and c) the regular CA certificate. To fix that error, fix the reason for a) or b) or if this reason is intended, import the regular CA certificate to the browsers trusted CA store.
b) is a special case and the error is preventing a user from accessing a potentially compromised web server connection with a fake certificate that the client might actually trust. FortiGate will then display the untrusted CA signed connection and the end user will usually stop at the error message.
More info on certificates:
Best regards,
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here you need to put the policy ID which you can find in the GUI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
You can also check the below details to fix this issue
-
Check that the SSL certificate used by the Fortinet device is valid and has not expired. If the certificate has expired, you will need to renew it.
-
Verify that the SSL certificate is issued by a trusted Certificate Authority (CA). If it is not, you may need to install the CA's root certificate on your computer or network to trust the SSL certificate used by the Fortinet device.
-
Try accessing the Fortinet device using a different web browser. Sometimes, the SSL certificate issue may be browser-specific.
-
Check that the date and time on your computer are correct. If the date and time are incorrect, it may cause SSL certificate errors.
Regards,
Shilpa
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- FortiGate automation - Send email or... 685 Views
- Fortimanager upgrade of ADOM from 7.0... 144 Views
- Error connecting to a VPN takes... 118 Views
- 30000 ms timeout waiting for FortiClient... 117 Views
- Forti vpn not installed 128 Views
-
Fortigate
7,448 -
FortiClient
1,469 -
5.2
801 -
5.4
639 -
FortiManager
637 -
FortiAnalyzer
484 -
6.0
416 -
FortiSwitch
387 -
FortiAP
386 -
5.6
362 -
FortiClient EMS
312 -
FortiMail
287 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
181 -
FortiNAC
134 -
SSL-VPN
129 -
6.4
128 -
IPsec
124 -
FortiGuard
121 -
FortiGateCloud
97 -
FortiCloud Products
93 -
FortiSIEM
92 -
FortiToken
80 -
Customer Service
72 -
Wireless Controller
68 -
SD-WAN
65 -
4.0MR3
64 -
FortiProxy
53 -
FortiEDR
47 -
Fortivoice
46 -
FortiADC
46 -
FortiDNS
43 -
FortiAuthenticator
43 -
Firewall policy
40 -
FortiSandbox
38 -
VLAN
38 -
FortiExtender
37 -
FortiGate v5.4
36 -
FortiSwitch v6.4
32 -
High Availability
32 -
DNS
28 -
BGP
27 -
LDAP
27 -
FortiConnect
26 -
ZTNA
26 -
FortiGate v5.2
24 -
FortiWAN
24 -
FortiConverter
23 -
SAML
22 -
Interface
22 -
Authentication
21 -
Routing
21 -
Certificate
21 -
FortiSwitch v6.2
20 -
FortiLink
19 -
NAT
19 -
FortiPortal
18 -
VDOM
18 -
RADIUS
16 -
Logging
16 -
FortiMonitor
16 -
Virtual IP
16 -
Web profile
16 -
FortiGate v5.0
15 -
SSL SSH inspection
15 -
Fortigate Cloud
14 -
FortiDDoS
14 -
Application control
14 -
Traffic shaping
13 -
FortiManager v5.0
12 -
FortiCASB
12 -
SSO
12 -
IP address management - IPAM
11 -
FortiRecorder
10 -
SSID
10 -
Static route
10 -
4.0MR2
9 -
FortiGate v4.0 MR3
9 -
FortiAnalyzer v5.0
9 -
FortiSOAR
9 -
FortiWeb v5.0
9 -
SNMP
9 -
RMA Information and Announcements
9 -
OSPF
9 -
FortiAP profile
9 -
WAN optimization
9 -
FortiManager v4.0
8 -
FortiBridge
8 -
Admin
8 -
Security profile
8 -
Proxy policy
8 -
Web application firewall profile
8 -
4.0
7 -
FortiCache
7 -
Automation
7 -
trunk
6 -
IPS signature
6 -
Antivirus profile
6 -
Traffic shaping policy
6 -
System settings
6 -
FortiCarrier
5 -
FortiDirector
5 -
DNS Filter
5 -
Packet capture
5 -
FortiTester
5 -
Users
5 -
Port policy
5 -
Intrusion prevention
5 -
Fortinet Engage Partner Program
5 -
3.6
4 -
FortiDeceptor
4 -
FortiScan
4 -
Explicit proxy
4 -
FortiPAM
4 -
Traffic shaping profile
4 -
Application signature
4 -
DLP sensor
4 -
DoS policy
4 -
Web rating
4 -
FortiInsight
3 -
FortiDB
3 -
FortiCWP
3 -
FortiToken Cloud
3 -
FortiHypervisor
3 -
NAC policy
3 -
Authentication rule and scheme
3 -
DLP Dictionary
3 -
DLP profile
3 -
Email filter profile
3 -
Fabric connector
3 -
File filter
3 -
Multicast routing
3 -
FortiAI
2 -
FortiNDR
2 -
Internet Service Database
2 -
Netflow
2 -
Protocol option
2 -
Replacement messages
2 -
Schedule
2 -
Service
2 -
VoIP profile
2 -
Zone
2 -
4.0MR1
1 -
FortiManager-VM
1 -
Kerberos
1 -
RIP
1 -
Subscription Renewal Policy
1 -
Video Filter
1 -
TACACS
1 -
SDN connector
1 -
Multicast policy
1
| User | Count |
|---|---|
| 1238 | |
| 932 | |
| 674 | |
| 441 | |
| 176 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.