- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiAP
- FortiADC
- FortiAnalyzer
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDDoS
- FortiDAST
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiGate Cloud
- FortiExtender
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiWebCloud
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- Drop failover sessions when link comes back up
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Drop failover sessions when link comes back up
I have a 60D running 5.2.3. I have two WAN connections, one for all the VoIP and the other for all other data. The VoIP network moves all it traffic out the voice WAN and all other networks move data out the data WAN. If the voice WAN goes down then all the voice traffic is rerouted out the data WAN. When the voice WAN comes back up the traffic is rerouted back to the voice WAN. The same goes for the data WAN when it fails, it goes to the voice WAN then back to the data WAN when it comes back up. I have all this working as expected right now.
My problem is that when the WAN link is restored none of the failed over sessions are rerouted back to their proper interface until there is a new session created. This means that it is possible for traffic to be routed out the wrong interface for a long time. How do I get these fail over sessions to terminate and create new sessions going out the proper WAN interface when that WAN interface comes back up? I can do this with my Cisco router automatically, but I need to get this same behavior with the Fortigate.
Thank you in advance,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ddemland wrote:I have a 60D running 5.2.3. I have two WAN connections, one for all the VoIP and the other for all other data. The VoIP network moves all it traffic out the voice WAN and all other networks move data out the data WAN. If the voice WAN goes down then all the voice traffic is rerouted out the data WAN. When the voice WAN comes back up the traffic is rerouted back to the voice WAN. The same goes for the data WAN when it fails, it goes to the voice WAN then back to the data WAN when it comes back up. I have all this working as expected right now.
My problem is that when the WAN link is restored none of the failed over sessions are rerouted back to their proper interface until there is a new session created. This means that it is possible for traffic to be routed out the wrong interface for a long time. How do I get these fail over sessions to terminate and create new sessions going out the proper WAN interface when that WAN interface comes back up? I can do this with my Cisco router automatically, but I need to get this same behavior with the Fortigate.
Thank you in advance,
David
AFAIK: That's the deault behaviour in FGT.
Once the session is created the FGT will keep using the same route for all the traffic for that session and does not perform a route lookup until the session is valid. (The FGT is offloading the session to NP, this improves the performance as FGT doesn't need to perform route lookups quite often.)
Once the session expires, when ever a new packet arrives the FGT will perform a route lookup and in this case it will assign the exit interface accordingly.
I would not recommend, but you could reduce the session life time or/and disable the offloading.
Hope it helps,
Prab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the information. However in most cases, that I have been exposed to, using two different connections are not only for fault tolerance but they also include cost differences and using one connection more often that expected incurs higher operation cost. I clearly understand the design and the reason for it, but not being able to restore normal operations quickly would lead to unexpected cost and other business operation issues.
What would be nice is if I could write a script that runs when an interface comes back up where I could kill sessions that need to be moved back to the primary path so that they are moved back to their primary path as fast as possible and still leave the device working as closely as it can to its design. This would allow me to "interfere" only with routes that have to be restored after and outage. Is there a way to accomplish this task?
Thank You,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Voice would regularly be routed to one IP, SBC. I would try setting filter with the IP for source then destination of sessions to clear them "diag sys session clear".
http://kb.fortinet.com/kb/documentLink.do?externalID=FD31635
You might need to "clear" a couple of time to clear all of them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ddemland wrote:Thank you for the information. However in most cases, that I have been exposed to, using two different connections are not only for fault tolerance but they also include cost differences and using one connection more often that expected incurs higher operation cost. I clearly understand the design and the reason for it, but not being able to restore normal operations quickly would lead to unexpected cost and other business operation issues.
What would be nice is if I could write a script that runs when an interface comes back up where I could kill sessions that need to be moved back to the primary path so that they are moved back to their primary path as fast as possible and still leave the device working as closely as it can to its design. This would allow me to "interfere" only with routes that have to be restored after and outage. Is there a way to accomplish this task?
Thank You,
David
You could try playing around with Link-monitoring or the SD-WAN feature in 5.6 FortiOS. Maybe you can customize it for your scenario, unfortunately I am not sure if it will solve your issue. You might just need to test it.
Ref: https://cookbook.fortinet.com/redundant-internet-basic-failover-56/
Regarding the script: I am not sure if you could do that solely on the FGT, you might need an additional tool that will (authenticate &) execute the script on the FGT's CLI via SSH/Telnet etc. Please refer to this post: https://forum.fortinet.com/tm.aspx?m=107230
Maybe Rest API might come to your rescue: https://forum.fortinet.com/tm.aspx?m=144649
Hope it helps,
Prab
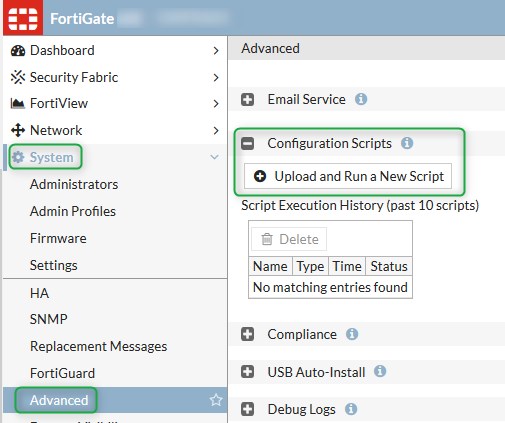
Edit: You can upload a script directly over the FGT's GUI. Have a look under System -> Advanced
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried enabling "snat-route-change"? I have exact same problem as you described (only difference is I use VPN and BGP for failover), and enabling this solved it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gerryeah wrote:Thank you! This worked for me with VoIP & VPN traffic that stay connected on the failover WAN.Have you tried enabling "snat-route-change"? I have exact same problem as you described (only difference is I use VPN and BGP for failover), and enabling this solved it.
https://kb.fortinet.com/k....do?externalID=FD40943
Created on 01-07-2022 09:04 AM Edited on 01-07-2022 09:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there!
I understand that this only works for Firewall rules where you have NAT configured, right? In my case I don't have them because I use SLA Performance with Loopback interface in both sites and I don't need to create firewall rules and it doesn't work. Any recommendations?
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think "snat-route-change" was introduced with 6.0.
But not clear your set up yet. You're now saying "both sites". So this is over two IPsec VPNs? Also the fail-over is controlled by Cisco behind FG60D?
Whatever the case I recommend upgraded the 60D to the latest 6.0.x first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
No, maybe I didn't make myself clear.
I'm on version 6.4.7, so there is no problem.
I have set up a performance SLA to our DataCenter via 2 ways, (IPsec tunnel & fibre optic). When the Fibre (main) goes down, the tunnel is up, but when it recovers the Firewall keeps the sessions and doesn't work correctly.
The problem is that I don't have NAT configured in the rules, as it is "internal" communication and doesn't go out to the Internet.
I don't want to add a SNAT to always have visibility of which is the correct source.
Do you know of any way to proceed with this kind of errors?
Maybe lowering the TTL?
Thanks in advance!
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- FortiGate action for system maintenance. 96 Views
- FortiGate SDWAN rule failover 158 Views
- FortiGate HA preempt 81 Views
- What is outgoing manual failover criteria? 126 Views
- Forticlient 7.4 got stuck on starting... 240 Views
-
FortiGate
7,099 -
FortiClient
1,399 -
5.2
801 -
5.4
639 -
FortiManager
615 -
FortiAnalyzer
449 -
6.0
416 -
FortiAP
373 -
FortiSwitch
368 -
5.6
362 -
FortiClient EMS
288 -
FortiMail
276 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
175 -
6.4
128 -
FortiNAC
124 -
FortiGuard
115 -
IPsec
107 -
SSL-VPN
100 -
FortiGateCloud
95 -
FortiSIEM
92 -
FortiCloud Products
88 -
FortiToken
76 -
Customer Service
71 -
Wireless Controller
64 -
4.0MR3
64 -
FortiProxy
49 -
SD-WAN
47 -
FortiADC
45 -
Fortivoice
44 -
FortiEDR
43 -
FortiDNS
38 -
FortiExtender
36 -
FortiGate v5.4
35 -
FortiAuthenticator
34 -
FortiSandbox
33 -
Firewall policy
33 -
FortiSwitch v6.4
32 -
VLAN
31 -
High Availability
31 -
DNS
24 -
FortiWAN
24 -
FortiConnect
24 -
ZTNA
23 -
BGP
21 -
FortiConverter
21 -
Certificate
20 -
SAML
19 -
FortiGate v5.2
19 -
FortiPortal
18 -
FortiSwitch v6.2
17 -
LDAP
17 -
Interface
17 -
VDOM
17 -
Routing
15 -
FortiMonitor
14 -
Authentication
14 -
FortiGate v5.0
14 -
FortiLink
14 -
Fortigate Cloud
14 -
Logging
14 -
FortiDDoS
13 -
RADIUS
12 -
FortiCASB
12 -
NAT
11 -
Web profile
11 -
Traffic shaping
10 -
Virtual IP
10 -
SSL SSH inspection
10 -
SSO
10 -
Application control
10 -
FortiRecorder
10 -
SSID
9 -
FortiWeb v5.0
9 -
FortiManager v5.0
9 -
WAN optimization
9 -
4.0MR2
9 -
IP address management - IPAM
8 -
FortiBridge
8 -
FortiGate v4.0 MR3
8 -
RMA Information and Announcements
7 -
FortiSOAR
7 -
FortiAnalyzer v5.0
7 -
SNMP
7 -
Web application firewall profile
7 -
Admin
7 -
4.0
7 -
Security profile
6 -
Proxy policy
6 -
Traffic shaping policy
6 -
FortiAP profile
6 -
OSPF
6 -
Static route
6 -
IPS signature
5 -
Packet capture
5 -
FortiPAM
5 -
Automation
5 -
trunk
5 -
FortiManager v4.0
5 -
FortiDirector
4 -
Port policy
4 -
Antivirus profile
4 -
DNS Filter
4 -
FortiTester
4 -
FortiCarrier
4 -
FortiCache
4 -
3.6
4 -
FortiScan
4 -
Web rating
4 -
Intrusion prevention
4 -
FortiDeceptor
3 -
NAC policy
3 -
Multicast routing
3 -
System settings
3 -
Fortinet Engage Partner Program
3 -
FortiToken Cloud
3 -
Traffic shaping profile
3 -
DLP sensor
3 -
FortiDB
3 -
DoS policy
3 -
Email filter profile
3 -
Netflow
2 -
FortiInsight
2 -
Users
2 -
Protocol option
2 -
FortiAI
2 -
Application signature
2 -
FortiHypervisor
2 -
DLP Dictionary
2 -
VoIP profile
2 -
DLP profile
2 -
Fabric connector
2 -
Multicast policy
1 -
4.0MR1
1 -
Zone
1 -
Subscription Renewal Policy
1 -
FortiCWP
1 -
FortiNDR
1 -
TACACS
1 -
Replacement messages
1 -
Schedule
1 -
SDN connector
1 -
Authentication rule and scheme
1 -
FortiManager-VM
1 -
Internet Service Database
1 -
Explicit proxy
1
| User | Count |
|---|---|
| 1053 | |
| 870 | |
| 521 | |
| 441 | |
| 146 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.