- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiAP
- FortiADC
- FortiAnalyzer
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDDoS
- FortiDAST
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiGate Cloud
- FortiExtender
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiWebCloud
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- Re: Cant find 'Redirect all non-compliant/unregist...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cant find 'Redirect all non-compliant/unregistered FortiClient devices to captive portal'
I've been trying to test out the FortiClient NAC control lately and have come to a dead end trying to get non-compliant devices to be directed to a captive portal (where it explains how they don't have FortiClient installed and gives them a link).
Page 1746 of the 5.2 handbook says that "If the security policy has Redirect all non-compliant/unregistered FortiClient compatible devices to a captive portal enabled, users of non-compliant devices are redirected to a captive portal that is defined by the Endpoint NAC Download Portal replacement message",
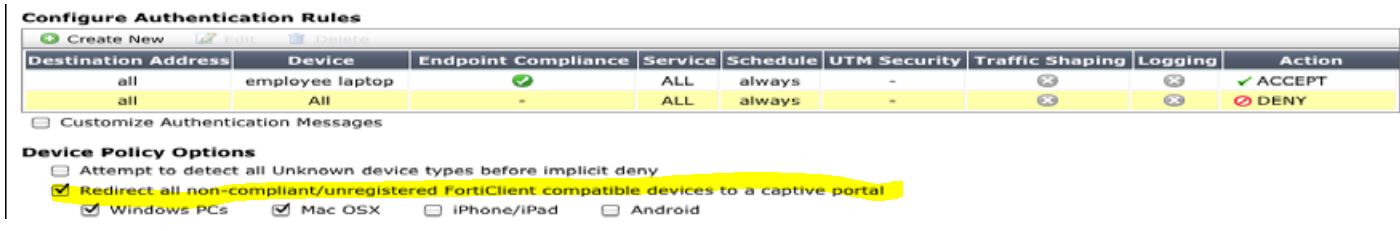
The problem is that on 5.2.2 this option doesn't seem to exist in the webGUI or the CLI. In FortiOS 5.0 this option is available in the GUI (picture attached).
Has anyone tested this out or knows howto enable this option on 5.2?
- Labels:
-
5.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See endpoint-compliance and endpoint-check option under Policy/policy6.
NSE4/FMG-VM64/FortiAnalyzer-VM/6.0 (FWF30E/FW92D/FGT200D/FGT101E/FGT81E)/ FAP220B/221C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks David, unfortunately the endpoint-check option isn't available in my policy, only the endpoint-compliance is there.
fortigate (32) # set endpoint-check enable
command parse error before 'endpoint-check' Command fail. Return code -61
Even when I do the 'tree' command in the policy I can't see an option for endpoint-check.
fortigate (32) # tree
-- [policy] --*policyid (0,4294967294)
|- uuid
|- [srcintf] --*name (65)
|- [dstintf] --*name (65)
|- [srcaddr] --*name (65)
|- [dstaddr] --*name (65)
|- rtp-nat
|- [rtp-addr] --*name (65)
|- action
|- send-deny-packet
|- firewall-session-dirty
|- status
|- schedule (36)
|- schedule-timeout
|- [service] --*name (65)
|- utm-status
|- profile-type
|- profile-group (36)
|- av-profile (36)
|- webfilter-profile (36)
|- spamfilter-profile (36)
|- dlp-sensor (36)
|- ips-sensor (36)
|- application-list (36)
|- voip-profile (36)
|- icap-profile (36)
|- profile-protocol-options (36)
|- ssl-ssh-profile (36)
|- logtraffic
|- logtraffic-start
|- capture-packet
|- wanopt
|- wanopt-detection
|- wanopt-passive-opt
|- wanopt-profile (36)
|- wanopt-peer (36)
|- webcache
|- webcache-https
|- traffic-shaper (36)
|- traffic-shaper-reverse (36)
|- per-ip-shaper (36)
|- nat
|- permit-any-host
|- permit-stun-host
|- fixedport
|- ippool
|- [poolname] --*name (65)
|- central-nat
|- session-ttl (0,0)
|- vlan-cos-fwd (0,0)
|- vlan-cos-rev (0,0)
|- inbound
|- outbound
|- natinbound
|- natoutbound
|- wccp
|- ntlm
|- ntlm-guest
|- [ntlm-enabled-browsers] --*user-agent-string (65)
|- fsso
|- wsso
|- rsso
|- fsso-agent-for-ntlm (36)
|- [groups] --*name (65)
|- [users] --*name (65)
|- [devices] --*name (36)
|- auth-path
|- disclaimer
|- vpntunnel (36)
|- natip
|- match-vip
|- diffserv-forward
|- diffserv-reverse
|- diffservcode-forward
|- diffservcode-rev
|- tcp-mss-sender (0,65535)
|- tcp-mss-receiver (0,65535)
|- comments
|- label (64 xss)
|- global-label (64 xss)
|- auth-cert (36)
|- auth-redirect-addr (64)
|- redirect-url (128)
|- identity-based-route (36)
|- block-notification
|- [custom-log-fields] --*field_id (36)
|- [tags] --*name (65)
|- replacemsg-override-group (36)
|- srcaddr-negate
|- dstaddr-negate
|- service-negate
|- endpoint-compliance
|- timeout-send-rst
+- captive-portal-exempt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What happens if you enable endpoint-compliance first? Some "sub" options don't even show up unless you enable a main or master option.
NSE4/FMG-VM64/FortiAnalyzer-VM/6.0 (FWF30E/FW92D/FGT200D/FGT101E/FGT81E)/ FAP220B/221C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nope, it still doesn't show up even when endpoint-compliance is enabled :(
config firewall policy
edit 32
set uuid ad2d9656-7ea1-51e4-cfd2-318694170163
set srcintf "port2"
set dstintf "port1"
set srcaddr "n_int"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set utm-status enable
set logtraffic all
set devices "all"
set endpoint-compliance enable
set av-profile "default"
set webfilter-profile "block-malware"
set spamfilter-profile "default"
set ips-sensor "protect_client"
set application-list "default"
set profile-protocol-options "default"
set ssl-ssh-profile "certificate-inspection"
set nat enable
next
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was a solution every found out for this? I am having the same issue where i have no option to redirect non-compliant devices to a captive portal.
I have my FortiClient working great with an SSL VPN connection but I want to redirect any devices that are not using the FortiClient to connect to a captive portal telling them to download the FortiClient.
Any help with this would be much appreciated I am running 5.2.3
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- Can't open console Forticlient VPN 7.4... 99 Views
- Stuck on Connecting after clicking the... 143 Views
- Forticlient (ZTNA) for ARM? 106 Views
- Problem with DLP on Fortigate 60E 210 Views
- Fedora 40 can not connect to... 71 Views
-
FortiGate
7,099 -
FortiClient
1,399 -
5.2
801 -
5.4
639 -
FortiManager
615 -
FortiAnalyzer
449 -
6.0
416 -
FortiAP
373 -
FortiSwitch
368 -
5.6
362 -
FortiClient EMS
288 -
FortiMail
276 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
175 -
6.4
128 -
FortiNAC
124 -
FortiGuard
115 -
IPsec
107 -
SSL-VPN
100 -
FortiGateCloud
95 -
FortiSIEM
92 -
FortiCloud Products
88 -
FortiToken
76 -
Customer Service
71 -
Wireless Controller
64 -
4.0MR3
64 -
FortiProxy
49 -
SD-WAN
47 -
FortiADC
45 -
Fortivoice
44 -
FortiEDR
43 -
FortiDNS
38 -
FortiExtender
36 -
FortiGate v5.4
35 -
FortiAuthenticator
34 -
FortiSandbox
33 -
Firewall policy
33 -
FortiSwitch v6.4
32 -
VLAN
31 -
High Availability
31 -
DNS
24 -
FortiWAN
24 -
FortiConnect
24 -
ZTNA
23 -
BGP
21 -
FortiConverter
21 -
Certificate
20 -
SAML
19 -
FortiGate v5.2
19 -
FortiPortal
18 -
FortiSwitch v6.2
17 -
LDAP
17 -
Interface
17 -
VDOM
17 -
Routing
15 -
FortiMonitor
14 -
Authentication
14 -
FortiGate v5.0
14 -
FortiLink
14 -
Fortigate Cloud
14 -
Logging
14 -
FortiDDoS
13 -
RADIUS
12 -
FortiCASB
12 -
NAT
11 -
Web profile
11 -
Traffic shaping
10 -
Virtual IP
10 -
SSL SSH inspection
10 -
SSO
10 -
Application control
10 -
FortiRecorder
10 -
SSID
9 -
FortiWeb v5.0
9 -
FortiManager v5.0
9 -
WAN optimization
9 -
4.0MR2
9 -
IP address management - IPAM
8 -
FortiBridge
8 -
FortiGate v4.0 MR3
8 -
RMA Information and Announcements
7 -
FortiSOAR
7 -
FortiAnalyzer v5.0
7 -
SNMP
7 -
Web application firewall profile
7 -
Admin
7 -
4.0
7 -
Security profile
6 -
Proxy policy
6 -
Traffic shaping policy
6 -
FortiAP profile
6 -
OSPF
6 -
Static route
6 -
IPS signature
5 -
Packet capture
5 -
FortiPAM
5 -
Automation
5 -
trunk
5 -
FortiManager v4.0
5 -
FortiDirector
4 -
Port policy
4 -
Antivirus profile
4 -
DNS Filter
4 -
FortiTester
4 -
FortiCarrier
4 -
FortiCache
4 -
3.6
4 -
FortiScan
4 -
Web rating
4 -
Intrusion prevention
4 -
FortiDeceptor
3 -
NAC policy
3 -
Multicast routing
3 -
System settings
3 -
Fortinet Engage Partner Program
3 -
FortiToken Cloud
3 -
Traffic shaping profile
3 -
DLP sensor
3 -
FortiDB
3 -
DoS policy
3 -
Email filter profile
3 -
Netflow
2 -
FortiInsight
2 -
Users
2 -
Protocol option
2 -
FortiAI
2 -
Application signature
2 -
FortiHypervisor
2 -
DLP Dictionary
2 -
VoIP profile
2 -
DLP profile
2 -
Fabric connector
2 -
Multicast policy
1 -
4.0MR1
1 -
Zone
1 -
Subscription Renewal Policy
1 -
FortiCWP
1 -
FortiNDR
1 -
TACACS
1 -
Replacement messages
1 -
Schedule
1 -
SDN connector
1 -
Authentication rule and scheme
1 -
FortiManager-VM
1 -
Internet Service Database
1 -
Explicit proxy
1
| User | Count |
|---|---|
| 1053 | |
| 870 | |
| 521 | |
| 441 | |
| 146 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.