- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiConnect
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDB
- FortiDDoS
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGuard
- FortiGate Cloud
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiPhish
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiWAN
- FortiVoice
- FortiWeb
- FortiWebCloud
- Lacework
- RMA Information and Announcements
- Wireless Controller
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- RE: Other router for other subnet / ICMP redirect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Other router for other subnet / ICMP redirect
Nominate a Forum Post for Knowledge Article Creation
Nominating a forum post submits a request to create a new Knowledge Article based on the forum post topic. Please ensure your nomination includes a solution within the reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bob - self proclaimed posting junkie!
See my Fortigate related scripts at: http://fortigate.camerabob.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
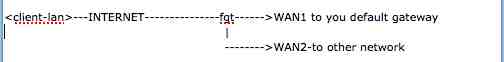
PCNSE
NSE
StrongSwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bob - self proclaimed posting junkie!
See my Fortigate related scripts at: http://fortigate.camerabob.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- Fortigate Unnumbered IP in PPPoE-client 583 Views
- FortiGate for testing in internal network 392 Views
- Static public IP / 2nd subnet... 322 Views
- FortiGate 7.4.4 VM IPv6 Prefix Delegation... 483 Views
- Help Needed: DDNS Not Working and... 1029 Views
-
FortiGate
8,006 -
FortiClient
1,606 -
5.2
801 -
FortiManager
677 -
5.4
639 -
FortiAnalyzer
515 -
FortiSwitch
423 -
FortiAP
421 -
6.0
416 -
5.6
362 -
FortiClient EMS
362 -
FortiMail
300 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
187 -
SSL-VPN
174 -
FortiNAC
159 -
IPsec
154 -
6.4
128 -
FortiGuard
124 -
FortiGateCloud
98 -
FortiCloud Products
94 -
FortiSIEM
93 -
SD-WAN
88 -
FortiToken
86 -
Customer Service
74 -
Wireless Controller
74 -
FortiAuthenticator
68 -
4.0MR3
64 -
Firewall policy
53 -
FortiProxy
52 -
FortiEDR
50 -
Fortivoice
49 -
FortiADC
49 -
FortiExtender
43 -
VLAN
42 -
FortiDNS
41 -
High Availability
40 -
FortiSandbox
39 -
ZTNA
37 -
FortiGate v5.4
35 -
Routing
34 -
LDAP
34 -
FortiSwitch v6.4
33 -
DNS
33 -
BGP
32 -
SAML
31 -
Certificate
30 -
Interface
29 -
SSO
27 -
NAT
26 -
FortiConnect
25 -
Authentication
25 -
FortiWAN
24 -
FortiConverter
24 -
RADIUS
24 -
FortiGate v5.2
23 -
VDOM
23 -
FortiLink
22 -
Virtual IP
20 -
Web profile
20 -
FortiSwitch v6.2
18 -
FortiPortal
18 -
Fortigate Cloud
18 -
Logging
18 -
FortiMonitor
16 -
Traffic shaping
16 -
Application control
16 -
FortiDDoS
15 -
FortiPAM
15 -
FortiGate v5.0
14 -
SSL SSH inspection
14 -
OSPF
13 -
FortiCASB
12 -
SSID
12 -
IP address management - IPAM
12 -
FortiManager v5.0
11 -
Automation
11 -
Admin
11 -
Static route
11 -
WAN optimization
11 -
Web application firewall profile
11 -
FortiRecorder
10 -
SNMP
10 -
4.0MR2
9 -
FortiSOAR
9 -
FortiWeb v5.0
9 -
FortiAP profile
9 -
FortiGate v4.0 MR3
8 -
FortiManager v4.0
8 -
FortiBridge
8 -
IPS signature
8 -
System settings
8 -
Proxy policy
8 -
4.0
7 -
FortiAnalyzer v5.0
7 -
RMA Information and Announcements
7 -
Traffic shaping policy
7 -
FortiCache
6 -
DNS filter
6 -
trunk
6 -
Packet capture
6 -
Security profile
6 -
Port policy
6 -
Intrusion prevention
6 -
FortiCarrier
5 -
FortiToken Cloud
5 -
FortiTester
5 -
Users
5 -
Fabric connector
5 -
3.6
4 -
FortiDeceptor
4 -
FortiScan
4 -
FortiDirector
4 -
Internet service database
4 -
Antivirus profile
4 -
Traffic shaping profile
4 -
DLP sensor
4 -
Email filter profile
4 -
Web rating
4 -
Fortinet Engage Partner Program
4 -
FortiDB
3 -
FortiHypervisor
3 -
Explicit proxy
3 -
NAC policy
3 -
DLP Dictionary
3 -
DLP profile
3 -
DoS policy
3 -
Netflow
3 -
Replacement messages
3 -
VoIP profile
3 -
Multicast routing
3 -
FortiInsight
2 -
FortiAI
2 -
API
2 -
FortiNDR
2 -
Application signature
2 -
Authentication rule and scheme
2 -
Protocol option
2 -
Schedule
2 -
Service
2 -
Zone
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Kerberos
1 -
Subscription Renewal Policy
1 -
Video Filter
1 -
TACACS
1 -
SDN connector
1 -
Multicast policy
1 -
Cloud Management Security
1
| User | Count |
|---|---|
| 1468 | |
| 1006 | |
| 748 | |
| 443 | |
| 206 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.