- Forums
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiBridge
- FortiAuthenticator
- FortiCache
- FortiCarrier
- FortiConnect
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDB
- FortiDDoS
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGuard
- FortiGate Cloud
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiMonitor
- FortiManager
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiPhish
- FortiProxy
- FortiRecorder
- FortiRecon
- FortiSandbox
- FortiScan
- FortiSASE
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiWAN
- FortiVoice
- FortiWeb
- FortiWebCloud
- Lacework
- RMA Information and Announcements
- Wireless Controller
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- FortiOS 6.2.3 is out
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FortiOS 6.2.3 is out
Nominate a Forum Post for Knowledge Article Creation
Nominating a forum post submits a request to create a new Knowledge Article based on the forum post topic. Please ensure your nomination includes a solution within the reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here, 6.2.3 is solid and works great.
Ken Felix
PCNSE
NSE
StrongSwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have both on but on all medium size 200 and 300Es, so it looks good for now. Will keep monitor.
Ken Felix
PCNSE
NSE
StrongSwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ede_pfau wrote:Hi Ede, Today I upgraded to 6.2.3: 2x 81E HA - from version 6.0.8, all without any problems (SSL VPN, IPsec VPN, without UTM) 1x 61E - from version 6.0.8, all without any problems (SSL VPN, IPsec VPN, full UTM)thanks for responding - neither do I, I prefer to use a FAZ instead of an x1 model, better investment even in the short run...
everything is connected to FAZ200D, 6.0.7
only where I had in Custom device group in Policy after the update it changed to "all" - watch it.
Jirka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
I have found an issue with 6.2.3 where emails with attachments sent from Outlook using SMTPS (465) were blocked. After disabling the UTM checks on the outbound policy the email functions returned to normal.
This firewall was upgraded Sunday the 12th, and the problem appeared on Monday morning the 13th. No other changes were performed on the firewall apart from the upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Upgraded FGT-92D from 6.2.2 build 1010 to 6.2.3 build 1066 and had a few issues.
1. SSL management stopped working - there were no logs regarding httpsd startup failiure; system global admin-server-cert was empty - had to reconfigure it from SSH;
2. Ever since the update (and later downgrade to 6.2.2) SSH key is recreated after a reboot. Can't find a log regarding it either;
3. The system is using PPPoE on uplink, had to manually change MTU on an email server behind it; downgrading back to 6.2.2 resolved the issue;
4. Have some issues with ipsec site2site connection, still looking what might be the cause.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re IPSEC - it might be the same as issue I found - had to add the following to config vpn ipsec phase1-interface
set net-device disable
I think 6.2.3 has an undocumented change in default behavior and now enabled the setting by default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
I have found an issue with 6.2.3 where emails with attachments sent from Outlook using SMTPS (465) were blocked. After disabling the UTM checks on the outbound policy the email functions returned to normal.
This firewall was upgraded Sunday the 12th, and the problem appeared on Monday morning the 13th. No other changes were performed on the firewall apart from the upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
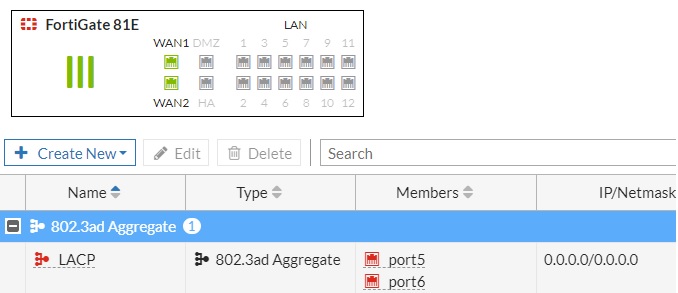
sigmasoftcz wrote:Hi Ede, yes, they do
[attachImg]https://forum.fortinet.com/download.axd?file=0;181980&where=message&f=lacp.jpg[/attachImg]
Jirka
Can you check if they now have "Redundant Interfaces" also?
Adding LACP support, that is technically way more complicated, but not simple port redundancy would be illogical.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am pretty much sure there's an issue or a change in packet processing defaults regarding packet size/mtu/fragmentation between FortiOS 6.2.2 and 6.2.3. I am using FGT92D with PPPoE uplink (8 bytes of overhead) on an ordinary Ethernet link (1500 MTU). The system is a gateway for some TCP baced services (SSH, SMTP, POP3, IMAP, HTTPS, RDP, ...) behind a NAT (RFC1918 network) and when updating from 6.2.2 to 6.2.3 the connection drops when trying to let's say send an email over TLS, or even doing a "show full-configuration" over couple of SSH connections. I opened a ticket and did multiple tests with TAC Engineer and I am able to reproduce the issue every time when upgrading to 6.2.3. I could change tcp-mss-* values in every policy and/or set tcp-mss on an interface, but i'd really like the system would have the same processing of packets as it did in 6.2.2. Could someone that has a lab environment confirm this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jirka:
Hi Ede, yes, they dogreat! Good news for us desktop model users. Thanks a lot for testing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
justme wrote:I am pretty much sure there's an issue or a change in packet processing defaults regarding packet size/mtu/fragmentation between FortiOS 6.2.2 and 6.2.3.
I've the same behaviour with a 100F and PPPoE WAN Connection. Back to 6.2.2 and it's working again.
Select Forum Responses to become Knowledge Articles!
Select the “Nominate to Knowledge Base” button to recommend a forum post to become a knowledge article.
- upgrade batch of FGT 6.4.6 to... 52 Views
- ZTNA within a 2 site setup... 59 Views
- Printing Over ZTNA Proxy 84 Views
- FortiSwitch not Applying Configuration from FortiGate 135 Views
- Invalid DHCP range. Start address is... 251 Views
-
FortiGate
8,005 -
FortiClient
1,606 -
5.2
801 -
FortiManager
677 -
5.4
639 -
FortiAnalyzer
515 -
FortiSwitch
423 -
FortiAP
421 -
6.0
416 -
5.6
362 -
FortiClient EMS
362 -
FortiMail
300 -
6.2
251 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
187 -
SSL-VPN
174 -
FortiNAC
159 -
IPsec
154 -
6.4
128 -
FortiGuard
124 -
FortiGateCloud
98 -
FortiCloud Products
94 -
FortiSIEM
93 -
SD-WAN
88 -
FortiToken
86 -
Customer Service
74 -
Wireless Controller
74 -
FortiAuthenticator
68 -
4.0MR3
64 -
Firewall policy
53 -
FortiProxy
52 -
FortiEDR
50 -
Fortivoice
49 -
FortiADC
49 -
FortiExtender
43 -
VLAN
42 -
FortiDNS
41 -
High Availability
40 -
FortiSandbox
39 -
ZTNA
37 -
FortiGate v5.4
35 -
Routing
34 -
LDAP
34 -
FortiSwitch v6.4
33 -
DNS
33 -
BGP
32 -
SAML
31 -
Certificate
30 -
Interface
29 -
SSO
27 -
NAT
26 -
FortiConnect
25 -
Authentication
25 -
FortiWAN
24 -
FortiConverter
24 -
RADIUS
24 -
FortiGate v5.2
23 -
VDOM
23 -
FortiLink
22 -
Virtual IP
20 -
Web profile
20 -
FortiSwitch v6.2
18 -
FortiPortal
18 -
Fortigate Cloud
18 -
Logging
18 -
FortiMonitor
16 -
Traffic shaping
16 -
Application control
16 -
FortiDDoS
15 -
FortiPAM
15 -
FortiGate v5.0
14 -
SSL SSH inspection
14 -
OSPF
13 -
FortiCASB
12 -
SSID
12 -
IP address management - IPAM
12 -
FortiManager v5.0
11 -
Automation
11 -
Admin
11 -
Static route
11 -
WAN optimization
11 -
Web application firewall profile
11 -
FortiRecorder
10 -
SNMP
10 -
4.0MR2
9 -
FortiSOAR
9 -
FortiWeb v5.0
9 -
FortiAP profile
9 -
FortiGate v4.0 MR3
8 -
FortiManager v4.0
8 -
FortiBridge
8 -
IPS signature
8 -
System settings
8 -
Proxy policy
8 -
4.0
7 -
FortiAnalyzer v5.0
7 -
RMA Information and Announcements
7 -
Traffic shaping policy
7 -
FortiCache
6 -
DNS filter
6 -
trunk
6 -
Packet capture
6 -
Security profile
6 -
Port policy
6 -
Intrusion prevention
6 -
FortiCarrier
5 -
FortiToken Cloud
5 -
FortiTester
5 -
Users
5 -
Fabric connector
5 -
3.6
4 -
FortiDeceptor
4 -
FortiScan
4 -
FortiDirector
4 -
Internet service database
4 -
Antivirus profile
4 -
Traffic shaping profile
4 -
DLP sensor
4 -
Email filter profile
4 -
Web rating
4 -
Fortinet Engage Partner Program
4 -
FortiDB
3 -
FortiHypervisor
3 -
Explicit proxy
3 -
NAC policy
3 -
DLP Dictionary
3 -
DLP profile
3 -
DoS policy
3 -
Netflow
3 -
Replacement messages
3 -
VoIP profile
3 -
Multicast routing
3 -
FortiInsight
2 -
FortiAI
2 -
API
2 -
FortiNDR
2 -
Application signature
2 -
Authentication rule and scheme
2 -
Protocol option
2 -
Schedule
2 -
Service
2 -
Zone
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Kerberos
1 -
Subscription Renewal Policy
1 -
Video Filter
1 -
TACACS
1 -
SDN connector
1 -
Multicast policy
1 -
Cloud Management Security
1
| User | Count |
|---|---|
| 1468 | |
| 1006 | |
| 748 | |
| 443 | |
| 206 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.