- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Forums
- Support Forum
- FortiAuthenticator ERROR: No mutually acceptable t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FortiAuthenticator ERROR: No mutually acceptable types found
Hello,
Im struggling with FortiAuthenticator and MAC bypass, cant make it work, I did read documentation, but havent found solution. My scenerio is very simple, (PC)->[TPlink_SW]->[FAC]. All are in the same network - its all for tests only.
EAP-TLS using certificate is working as expected. Endpoints has certs deployed. But There devices that dodnt support RADIUS(802.1x). Do you have any clue where can I search for solution? Im starting thinking that crapy tplink might be the problem. That Tplink dont understand strong auths or else.
Error Log:
2024-02-14T22:31:05.610504+01:00 FortiAuthenticator radiusd[26760]: (243) eap: Comparing client IP 172.16.1.240 with authclient 172.16.1.239 (172.16.1.239, 1 IPs)
2024-02-14T22:31:05.610510+01:00 FortiAuthenticator radiusd[26760]: (243) eap: Comparing client IP 172.16.1.240 with authclient 172.16.1.17 (172.16.1.17, 1 IPs)
2024-02-14T22:31:05.610515+01:00 FortiAuthenticator radiusd[26760]: (243) eap: Found authclient from preloaded authclients list for 172.16.1.240: 172.16.1.240 (172.16.1.240)
2024-02-14T22:31:05.610520+01:00 FortiAuthenticator radiusd[26760]: (243) eap: authclient_id:10 auth_type:'password'
2024-02-14T22:31:05.611030+01:00 FortiAuthenticator radiusd[26760]: (243) eap: WARNING: No authpolicy for authclient 10 with authtype password
2024-02-14T22:31:05.611037+01:00 FortiAuthenticator radiusd[26760]: (243) eap: ERROR: No mutually acceptable types found
2024-02-14T22:31:05.611050+01:00 FortiAuthenticator radiusd[26760]: (243) eap: Sending EAP Failure (code 4) ID 3 length 4
2024-02-14T22:31:05.611068+01:00 FortiAuthenticator radiusd[26760]: (243) eap: Failed in EAP select
2024-02-14T22:31:05.611074+01:00 FortiAuthenticator radiusd[26760]: (243) [eap] = invalid
2024-02-14T22:31:05.611079+01:00 FortiAuthenticator radiusd[26760]: (243) } # authenticate = invalid
2024-02-14T22:31:05.611085+01:00 FortiAuthenticator radiusd[26760]: (243) Failed to authenticate the user
2024-02-14T22:31:05.611094+01:00 FortiAuthenticator radiusd[26760]: (243) Using Post-Auth-Type Reject
2024-02-14T22:31:05.611101+01:00 FortiAuthenticator radiusd[26760]: (243) # Executing group from file /usr/etc/raddb/sites-enabled/default
2024-02-14T22:31:05.611106+01:00 FortiAuthenticator radiusd[26760]: (243) Post-Auth-Type REJECT {
2024-02-14T22:31:05.611139+01:00 FortiAuthenticator radiusd[26760]: (243) facauth: Updated auth log '501fc65bc05f': 802.1x authentication failed
2024-02-14T22:31:05.611146+01:00 FortiAuthenticator radiusd[26760]: (243) [facauth] = reject
2024-02-14T22:31:05.611151+01:00 FortiAuthenticator radiusd[26760]: (243) } # Post-Auth-Type REJECT = reject
2024-02-14T22:31:05.611159+01:00 FortiAuthenticator radiusd[26760]: (243) Delaying response for 1.000000 seconds
2024-02-14T22:31:05.611171+01:00 FortiAuthenticator radiusd[26760]: Thread 3 waiting to be assigned a request
2024-02-14T22:31:05.790200+01:00 FortiAuthenticator radiusd[26760]: (238) Cleaning up request packet ID 96 with timestamp +3116
2024-02-14T22:31:05.810172+01:00 FortiAuthenticator radiusd[26760]: (239) Cleaning up request packet ID 97 with timestamp +3116
2024-02-14T22:31:05.810183+01:00 FortiAuthenticator radiusd[26760]: Waking up in 0.4 seconds.
2024-02-14T22:31:06.278169+01:00 FortiAuthenticator radiusd[26760]: Waking up in 0.3 seconds.
2024-02-14T22:31:06.614204+01:00 FortiAuthenticator radiusd[26760]: (243) Sending delayed response
2024-02-14T22:31:06.614214+01:00 FortiAuthenticator radiusd[26760]: (243) Sent Access-Reject Id 101 from 172.16.1.250:1812 to 172.16.1.240:58403 length 44
2024-02-14T22:31:06.614221+01:00 FortiAuthenticator radiusd[26760]: (243) EAP-Message = 0x04030004
2024-02-14T22:31:06.614226+01:00 FortiAuthenticator radiusd[26760]: (243) Message-Authenticator = 0x00000000000000000000000000000000
2024-02-14T22:31:06.614247+01:00 FortiAuthenticator radiusd[26760]: Waking up in 18.5 seconds.
2024-02-14T22:31:25.218201+01:00 FortiAuthenticator radiusd[26760]: (240) Cleaning up request packet ID 98 with timestamp +3136
2024-02-14T22:31:25.218212+01:00 FortiAuthenticator radiusd[26760]: (241) Cleaning up request packet ID 99 with timestamp +3136
2024-02-14T22:31:25.218218+01:00 FortiAuthenticator radiusd[26760]: Waking up in 10.3 seconds.
2024-02-14T22:31:35.618205+01:00 FortiAuthenticator radiusd[26760]: (242) Cleaning up request packet ID 100 with timestamp +3146
2024-02-14T22:31:35.618215+01:00 FortiAuthenticator radiusd[26760]: (243) Cleaning up request packet ID 101 with timestamp +3146
2024-02-14T22:31:35.618221+01:00 FortiAuthenticator radiusd[26760]: Ready to process requests
- Labels:
-
FortiAuthenticator v5.5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
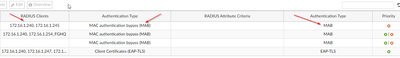
Have you created separate RADIUS policies for EAP-TLS and MAB and are the MAC authentication request hitting the right policy?
Regarding the TP link configuration keep in mind that there is also a MAC authentication method over EAP (EAP-MD5), make sure it uses the standard not encapsulated method.
You can run a packet capture to get more info from FAC CLI:
> execute tcpdump -i any port 1812
and download the capture from GUI: https://<fac>/debug/pcap-dump/
If you have found a solution, please like and accept it to make it easily accessible for others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
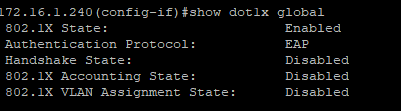
Good pooint to check tcpdump - will do that. Regarding SW - I can set only PAP or EAP. I do have policy for MAB of FAC, Sw ports are also configured to use "MAC Based"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So actually nothing explicitly displayed here ;)
17:23:34.206471 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x69 length: 128 17:23:34.207627 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Chal lenge (11), id: 0x69 length: 64 17:23:34.211661 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6a length: 135 17:23:35.214216 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reje ct (3), id: 0x6a length: 44 17:24:00.585100 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6b length: 128 17:24:00.586196 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Chal lenge (11), id: 0x6b length: 64 17:24:00.590620 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6c length: 135 17:24:01.594233 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reje ct (3), id: 0x6c length: 44 17:24:04.326067 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6d length: 128 17:24:04.327252 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Chal lenge (11), id: 0x6d length: 64 17:24:04.331071 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6e length: 135 17:24:05.334231 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reje ct (3), id: 0x6e length: 44 17:24:34.256675 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x6f length: 128 17:24:34.257754 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Chal lenge (11), id: 0x6f length: 64 17:24:34.261545 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Requ est (1), id: 0x70 length: 135 17:24:35.266251 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reje ct (3), id: 0x70 length: 44 17:25:34.193607 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Request (1), id: 0x71 length: 128 17:25:34.194649 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Challenge (11), id: 0x71 length: 64 17:25:34.198556 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Request (1), id: 0x72 length: 135 17:25:35.202219 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reject (3), id: 0x72 length: 44 17:26:00.583626 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Request (1), id: 0x73 length: 128 17:26:00.584668 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Challenge (11), id: 0x73 length: 64 17:26:00.592660 IP 172.16.1.240.58403 > 172.16.1.250.radius: RADIUS, Access-Request (1), id: 0x74 length: 135 17:26:01.598215 IP 172.16.1.250.radius > 172.16.1.240.58403: RADIUS, Access-Reject (3), id: 0x74 length: 44
Created on 02-15-2024 10:57 AM Edited on 02-15-2024 11:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
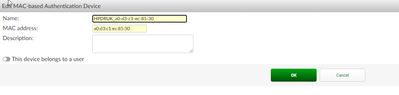
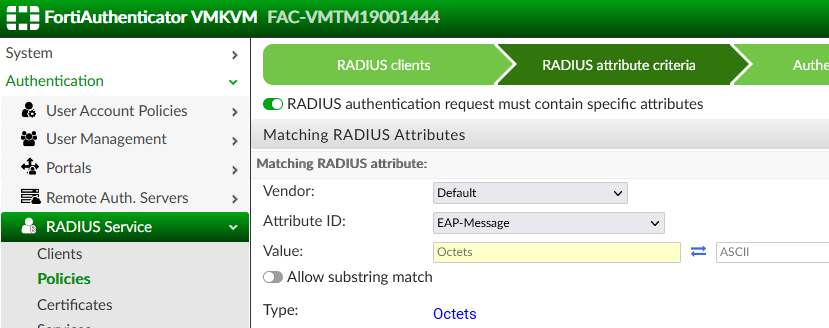
Here you have how policies look like and MAC for the device.
From given logs I cant see that its catching into my first policy.
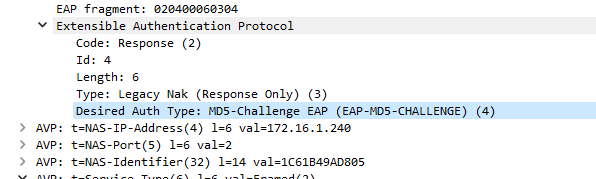
Did wireshark and I can notice that SW is trying to do MD5 challange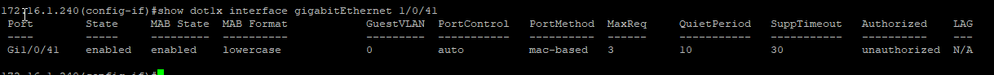
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it looks like the switch is doing MAC authentication over EAP tunnel. The simplest way is to change the configuration of the switch to do plain MAC authentication and not over EAP. Since the username and password is the MAC address that is already visible there is no added security in this case.
The second method could be using the filters in FAC RADIUS policies to distinguish between EAP-TLS and EAP-MD5
If you have found a solution, please like and accept it to make it easily accessible for others.
Created on 02-16-2024 01:11 AM Edited on 02-16-2024 01:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to clarify: The EAP method offers do not happen in the very first Access-Request message, thus policy-matching based on EAP-Message content will not work if its purpose is to match an EAP-MD5 request.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also I searched through the documentations and didn't find any hints that FAC support MAC authentication over EAP. I guess that the MAB authentication rule will not match if the RADIUS requests are coming as EAP.
The only way would be changing the configuration on the switch.
If you have found a solution, please like and accept it to make it easily accessible for others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'll test potential solution from given screenshot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh Thx, I'll take a look at it. May I ask you what exactly should I put into EAP-MSG? You mean type of auth request? or just EAP-MD5?
TPlink(unfortunately) is not capable to choose which protocol could be used for MAB. I can use PAP or EAP - There is no posibility to set it per port. On Cisco - yes, but as we know, its different league.
- Using Fortigate to Protect Web Server... 1966 Views
- Wifi authenticator using certificate 3397 Views
- Radius with EAP not working 7644 Views
- FortiClient to FortiGate SSL-VPN using SMS... 21250 Views
-
FortiGate
6,529 -
FortiClient
1,303 -
5.2
801 -
5.4
639 -
FortiManager
563 -
6.0
416 -
FortiAnalyzer
414 -
5.6
362 -
FortiSwitch
333 -
FortiAP
333 -
FortiClient EMS
263 -
6.2
251 -
FortiMail
242 -
FortiAuthenticator v5.5
234 -
5.0
196 -
FortiWeb
150 -
6.4
128 -
FortiNAC
106 -
FortiGuard
102 -
FortiSIEM
88 -
FortiGateCloud
87 -
FortiCloud Products
84 -
IPsec
73 -
FortiToken
69 -
Customer Service
69 -
4.0MR3
64 -
SSL-VPN
59 -
Wireless Controller
58 -
FortiProxy
44 -
FortiADC
42 -
Fortivoice
41 -
FortiEDR
39 -
FortiGate v5.4
34 -
FortiDNS
34 -
FortiExtender
31 -
FortiSandbox
31 -
FortiSwitch v6.4
28 -
SD-WAN
24 -
FortiConnect
23 -
FortiWAN
22 -
Firewall policy
22 -
FortiConverter
21 -
High Availability
20 -
VLAN
19 -
FortiPortal
18 -
ZTNA
16 -
FortiSwitch v6.2
16 -
FortiGate v5.2
16 -
FortiMonitor
14 -
Certificate
14 -
DNS
13 -
FortiDDoS
13 -
SAML
12 -
BGP
12 -
Routing
12 -
FortiAuthenticator
12 -
FortiCASB
12 -
Interface
11 -
Logging
11 -
FortiGate v5.0
10 -
LDAP
10 -
FortiRecorder
10 -
VDOM
10 -
FortiWeb v5.0
9 -
FortiManager v5.0
9 -
Virtual IP
9 -
NAT
9 -
4.0MR2
9 -
RADIUS
8 -
Traffic shaping
8 -
SSID
7 -
RMA Information and Announcements
7 -
FortiSOAR
7 -
fortilink
7 -
FortiAnalyzer v5.0
7 -
FortiGate v4.0 MR3
7 -
Admin
7 -
4.0
7 -
SSL SSH inspection
6 -
Security profile
6 -
Authentication
6 -
Fortigate Cloud
6 -
IP address management - IPAM
6 -
Traffic shaping policy
5 -
FortiBridge
5 -
SNMP
5 -
SSO
5 -
Application control
5 -
FortiManager v4.0
5 -
Static route
5 -
FortiDirector
4 -
WAN optimization
4 -
Web application firewall profile
4 -
DNS Filter
4 -
FortiTester
4 -
FortiCarrier
4 -
FortiCache
4 -
OSPF
4 -
3.6
4 -
FortiScan
4 -
Proxy policy
4 -
IPS signature
3 -
packet capture
3 -
FortiToken Cloud
3 -
FortiAP profile
3 -
Intrusion prevention
3 -
Automation
3 -
DoS policy
3 -
Port policy
3 -
FortiDB
3 -
FortiDeceptor
2 -
FortiInsight
2 -
NAC policy
2 -
VoIP profile
2 -
Antivirus profile
2 -
Web profile
2 -
Traffic shaping profile
2 -
FortiAI
2 -
FortiHypervisor
2 -
Netflow
2 -
Fortinet Engage Partner Program
2 -
trunk
2 -
SDN connector
1 -
4.0MR1
1 -
Users
1 -
Subscription Renewal Policy
1 -
FortiCWP
1 -
FortiNDR
1 -
Web rating
1 -
FortiPAM
1 -
Application signature
1 -
Multicast routing
1 -
Authentication rule and scheme
1 -
Zone
1 -
FortiManager-VM
1 -
Internet Service Database
1 -
System settings
1 -
Explicit proxy
1 -
TACACS
1
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.