- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Support Forum
- Fortigate Blocking some IPs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fortigate Blocking some IPs
Hi team,
I am facing a very strange issue. I configured fortigate 100E for one of my company`s client with 2 ISPs(without load balancing). Every thing works fine but some ips from LAN is blocking to get internet from WAN1 while the same hosts can reach the internet from WAN2.
I created 2 policies one LAN>WAN2 and 2nd LAN>WAN1. i want my all traffic get internet from WAN2 but some traffic passing out through WAN1. and some ips are blocking from WAN1.
LAN>WAN2 ( sources set to all ) .... while the 2nd policy is for failover. (sources set to all)
any suggestion...?????
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The problem is routing. If you have two default routes with equal cost/priority in the routing table, you don't have control which way to send out. The basic set-up for your situation is below. I haven't learned how to do the same with SD-WAN so ask somebody else if you prefer SD-WAN.
https://cookbook.fortinet...net-basic-failover-56/
PS. looks like they're moving cookbooks to the doc library. I hope they would be still searchable from search engines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Configure SD-WAN to achieve ur requirement , it is enhanced version of old WAN Link load balancer .You can have single policy and routing as well. For more information please refer below link
https://docs.fortinet.com/document/fortigate/6.0.0/cookbook/990932/redundant-internet-with-sd-wan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You've stated that you don't want to load-balance. In this case, assign a higher metric to the default route of your backup ISP. There will only be one default route now in the Routing monitor (Monitor > Routing Monitor) until ISP1 fails. Then the second, backup default route will be inserted and used.
Even source addresses going out WAN1 and odd ones going out WAN2 is a symptom of load balancing (which uses a hash of source address and source port, and something else).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks ede...
I did that before but issue is fortigate blocking some of ips ... when i configured only my wan2 and disabled wan1 those ips cant get internet regarless of machines only ips are blocking and when i configure only wan1 fortigate behave the same with some other ips. ( Blocked ips for wan1 and wan2 are diffrent).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ashu brother thanks.
this is not my first fortigate unit i deployed a bunch of devices for my different clients. for some sd-wan is good but here i need wan1 for email server as priority and wan2 for lan ( both are separate lans). but issue is fortigate is blocking some ips through both wans ( different ips for both wans).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Adil.
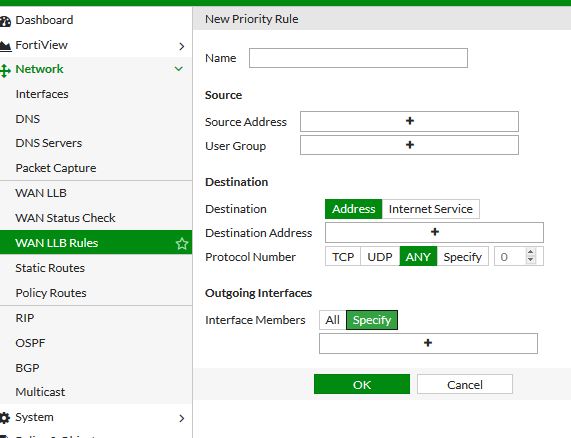
I'm kinda with the others on this with regards to using SD-WAN (or WAN LLB). You can pretty much direct traffic via priority rules out whichever Interface (e.g. WAN1, WAN2) as well is specific one of the ports for the email server.
That said, if you are adamant about keeping your existing setup, we need more information on your issue, like a network layout and/or what other troubleshooting has been done (e.g. like ruling out physical connection drops), packet trace, etc.
diag debug reset diag debug flow filter proto 6 diag debug flow filter addr <internal IP> diag debug flow show console enable diag debug flow trace start 1000 diag debug en
The only time I have heard something like this happening is when a sysadmin introduced a typo when entering the subnet range/mask for an address object.
NSE4/FMG-VM64/FortiAnalyzer-VM/6.0 (FWF30E/FW92D/FGT200D/FGT101E/FGT81E)/ FAP220B/221C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thankx dave Hall,
brother i did the debugging but no output of any command
and also the blocked ips successfully ping the gateway from where it is blocked
For example 192.168.1.128 is blocked from 192.168.100.1 ( PTCL Router gateway) but it can ping it successfully but cant get internet from it rather for internet it moved to other static ip gateway ( used for port forwarding). sory to forget the user is using AD Server for authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Toshi brother i don`t want SD-WAN because WAN1 is used for Email server port forwarding which is configured as a separate port with separate lan 172.16.10.0/24.
i made priorities using ipv4 policies.
fortigate uses the first available policy and i created first one LAN>WAN2 with sources all(initially). in this case fortigate should allow all traffic from LAN through wan2.
and 2nd LAN>WAN1 same with sources all.now if the wan2 is not available or reachable than fortigate unit move all traffic from wan1.but in this unit all traffic go through wan2 while some ips from wan1 because fortigate is blocking them from wan2
-
FortiGate
11,121 -
FortiClient
2,290 -
FortiManager
935 -
FortiAnalyzer
708 -
5.2
687 -
5.4
638 -
FortiClient EMS
616 -
FortiSwitch
614 -
FortiAP
580 -
IPsec
487 -
6.0
416 -
SSL-VPN
413 -
FortiMail
388 -
5.6
362 -
FortiNAC
321 -
FortiWeb
271 -
6.2
251 -
FortiAuthenticator v5.5
234 -
SD-WAN
218 -
FortiAuthenticator
197 -
FortiGate-VM
164 -
FortiGuard
164 -
Firewall policy
154 -
5.0
152 -
6.4
128 -
FortiCloud Products
122 -
FortiSIEM
118 -
FortiToken
118 -
FortiGateCloud
113 -
Wireless Controller
98 -
High Availability
97 -
Customer Service
91 -
SAML
85 -
Routing
85 -
ZTNA
84 -
FortiProxy
81 -
Authentication
79 -
FortiADC
76 -
VLAN
76 -
BGP
75 -
DNS
75 -
Certificate
75 -
Fortivoice
73 -
FortiEDR
73 -
RADIUS
69 -
LDAP
69 -
FortiLink
64 -
SSO
62 -
NAT
59 -
FortiSandbox
57 -
Interface
55 -
Application control
55 -
FortiExtender
53 -
VDOM
51 -
4.0MR3
49 -
Virtual IP
49 -
Logging
44 -
FortiDNS
43 -
FortiPAM
42 -
SSL SSH inspection
42 -
Web profile
39 -
FortiGate v5.4
38 -
FortiSwitch v6.4
38 -
FortiConnect
36 -
Automation
36 -
FortiConverter
33 -
FortiWAN
32 -
API
31 -
Traffic shaping
29 -
FortiGate v5.2
28 -
Static route
28 -
FortiGate Cloud
27 -
SNMP
26 -
SSID
26 -
OSPF
24 -
System settings
24 -
FortiSwitch v6.2
23 -
FortiPortal
23 -
Web application firewall profile
23 -
WAN optimization
22 -
FortiMonitor
21 -
IP address management - IPAM
21 -
Security profile
20 -
Web rating
20 -
FortiSOAR
19 -
FortiAP profile
18 -
Admin
17 -
Intrusion prevention
17 -
FortiGate v5.0
16 -
FortiDDoS
16 -
Explicit proxy
16 -
FortiManager v4.0
15 -
IPS signature
15 -
NAC policy
15 -
Users
15 -
Traffic shaping policy
15 -
Proxy policy
15 -
FortiManager v5.0
14 -
FortiCASB
14 -
DNS filter
13 -
FortiDeceptor
12 -
Fabric connector
12 -
Port policy
12 -
FortiWeb v5.0
11 -
FortiBridge
11 -
trunk
11 -
Traffic shaping profile
11 -
Authentication rule and scheme
11 -
FortiAnalyzer v5.0
10 -
FortiRecorder
10 -
Fortinet Engage Partner Program
10 -
FortiGate v4.0 MR3
9 -
RMA Information and Announcements
9 -
Antivirus profile
9 -
Application signature
9 -
FortiCache
8 -
FortiToken Cloud
8 -
Packet capture
8 -
Vulnerability Management
8 -
4.0
7 -
4.0MR2
7 -
FortiNDR
7 -
VoIP profile
7 -
FortiScan
6 -
FortiTester
6 -
DoS policy
6 -
FortiCarrier
5 -
DLP profile
5 -
DLP sensor
5 -
Email filter profile
5 -
Protocol option
5 -
TACACS
5 -
Service
5 -
Cloud Management Security
5 -
3.6
4 -
FortiDirector
4 -
Internet service database
4 -
DLP Dictionary
4 -
Netflow
4 -
Replacement messages
4 -
SDN connector
4 -
Multicast routing
4 -
FortiDB
3 -
FortiHypervisor
3 -
FortiAI
3 -
Kerberos
3 -
Video Filter
3 -
File filter
3 -
Multicast policy
3 -
FortiEdge Cloud
3 -
FortiInsight
2 -
Schedule
2 -
ICAP profile
2 -
Virtual wire pair
2 -
Zone
2 -
Lacework
2 -
FortiGuest
2 -
FortiEdge
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Subscription Renewal Policy
1 -
FortiSASE
1 -
FortiPresence
1 -
FortiAIOps
1
| User | Count |
|---|---|
| 2892 | |
| 1448 | |
| 848 | |
| 825 | |
| 455 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.