- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Support Forum
- Re: Combine PoE and internal interfaces on Fortiga...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Combine PoE and internal interfaces on Fortigate60D POE
I am new to Fortigate firewall management.
There is a lot to like about the 60DPoE but one thing I don't is Joining the 2 PoE interfaces to the internal switch.
What's the best way to combine the 2 PoE (InternalA, InternalB) and Internal (5 port switch).
I bought the 60D PoE because it had not only a configurable firewall but 2 PoE ports which would allow me to remove a Linksys PoE switch needed for 2 IP cameras.
The NVR is of course on the 5 port internal switch interface but the 2 PoE ports are required to be on different subnets.
The system works fine as long as I continue to run the IP cameras on a separate PoE switch using the internal 5 ports (all on the same subnet), but I need to get the 2 internalA internalB PoE ports mapped into the same subnet as the NVR. It seems like Fortinet would have an easy way to merge these interfaces. The 60D is basically configured to the factory default settings.
Ben
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not familiar with the 60D POE, but I assume you could still create a soft switch. Just make sure there are no references to the ports you want to create the soft switch. If the fgt has a clean/factory installed (e.g. exec factoryreset from CLI) you only need to delete the firewall policy for internal to "WAN", disable the DHCP on the internal. Then you should be able to create the soft switch from that point.
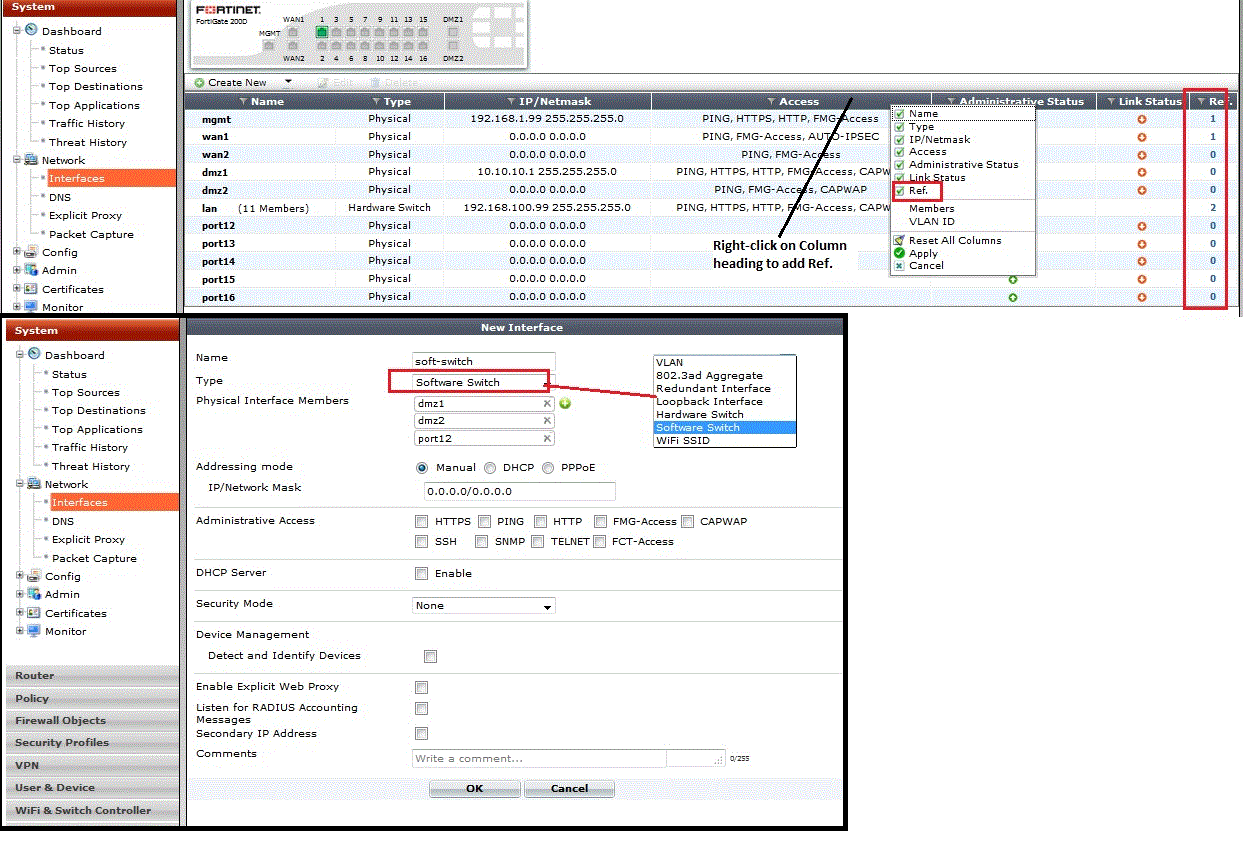
Alternately, if a soft switch is not doable, you may need to resort to setting up one or two VIPs then create a firewall policy (or two) between the internal and POE ports with NAT enabled. [strike](Kinda ugly imho.)[/strike]
Edit: Actually just creating two firewall polices between internal and the two poe ports with NAT enabled would also work.
NSE4/FMG-VM64/FortiAnalyzer-VM/6.0 (FWF30E/FW92D/FGT200D/FGT101E/FGT81E)/ FAP220B/221C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reading the Fortinet VIP documentation it sounds like they discourage VIP use in this way:
http://docs-legacy.fortin...lp/objects.067.08.html
----------------------------------------
Virtual IP addresses are typically used to NAT external or Public IP addresses to internal or Private IP addresses. [style="background-color: #ffff00;"]Using a Virtual IP address between 2 internal Interfaces made up of Private IP addresses is possible but there is rarely a reason to do so as the 2 networks can just use the IP addresses of the networks.[/style]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ben wrote:Reading the Fortinet VIP documentation it sounds like they discourage VIP use in this way:
http://docs-legacy.fortin...lp/objects.067.08.html
----------------------------------------
Virtual IP addresses are typically used to NAT external or Public IP addresses to internal or Private IP addresses. [style="background-color: #ffff00;"]Using a Virtual IP address between 2 internal Interfaces made up of Private IP addresses is possible but there is rarely a reason to do so as the 2 networks can just use the IP addresses of the networks.[/style]
Which is why edited my post to just using "natted" firewall policies if you can't use a soft switch.
NSE4/FMG-VM64/FortiAnalyzer-VM/6.0 (FWF30E/FW92D/FGT200D/FGT101E/FGT81E)/ FAP220B/221C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still looking for a solution to this. Any updates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tested with FWF60D-POE w/ 5.4.3. But I could make internalA as a member of the default soft switch (config sys switch-interface in CLI) interface "lan". I believe FG60D-OPE would behave the same. In case FWF, the default "lan" interface includes both "internal" hard switch (virtual-switch) interface and "wifi" vap-switch(SSID) interface. I just let internalA to join them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Toshi,
When I try that, the system responds "entry not found in datasource".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Found the solution in 5.4.3.
By default the internalA and internalB (POE Interfaces) are given their own unique IP (169.254..). In order to bond these interfaces to the internal network, I had to first zero out the IP address of the interface. Once the interface IP address is set to 0.0.0.0/0, it because available to add to the internal switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know you already figured out but we always remove the default IP by "unset ip" under the interface and remove DHCP for the interface "del n(depending on the entity number)" to move any interface config around.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can the internalA and internalB ports on a FortiWfi 60D POE be combined with the internal ports in a HARDWARE switch?
-
FortiGate
11,006 -
FortiClient
2,254 -
FortiManager
926 -
FortiAnalyzer
703 -
5.2
687 -
5.4
638 -
FortiSwitch
608 -
FortiClient EMS
604 -
FortiAP
577 -
IPsec
472 -
6.0
416 -
SSL-VPN
405 -
FortiMail
387 -
5.6
362 -
FortiNAC
315 -
FortiWeb
266 -
6.2
251 -
FortiAuthenticator v5.5
234 -
SD-WAN
215 -
FortiAuthenticator
195 -
FortiGuard
164 -
FortiGate-VM
156 -
5.0
152 -
Firewall policy
152 -
6.4
128 -
FortiCloud Products
122 -
FortiSIEM
116 -
FortiToken
115 -
FortiGateCloud
113 -
Wireless Controller
97 -
High Availability
95 -
Customer Service
91 -
SAML
84 -
Routing
84 -
ZTNA
82 -
FortiProxy
81 -
Authentication
76 -
VLAN
76 -
BGP
75 -
Fortivoice
74 -
DNS
74 -
Certificate
74 -
FortiEDR
73 -
FortiADC
71 -
RADIUS
68 -
LDAP
66 -
FortiLink
62 -
SSO
61 -
NAT
58 -
FortiSandbox
57 -
Interface
54 -
FortiExtender
53 -
Application control
52 -
VDOM
50 -
4.0MR3
49 -
Virtual IP
48 -
Logging
44 -
FortiDNS
43 -
SSL SSH inspection
42 -
FortiPAM
41 -
Web profile
39 -
FortiGate v5.4
38 -
FortiSwitch v6.4
38 -
FortiConnect
36 -
Automation
36 -
FortiWAN
32 -
FortiConverter
31 -
API
30 -
Traffic shaping
29 -
FortiGate v5.2
28 -
FortiGate Cloud
27 -
Static route
27 -
SSID
26 -
SNMP
25 -
System settings
24 -
FortiSwitch v6.2
23 -
FortiPortal
23 -
OSPF
23 -
WAN optimization
22 -
Web application firewall profile
22 -
FortiMonitor
21 -
Web rating
20 -
IP address management - IPAM
20 -
FortiSOAR
19 -
Security profile
19 -
FortiAP profile
18 -
FortiGate v5.0
16 -
FortiDDoS
16 -
Explicit proxy
16 -
Admin
16 -
IPS signature
15 -
Traffic shaping policy
15 -
Proxy policy
15 -
Intrusion prevention
15 -
FortiManager v4.0
14 -
FortiCASB
14 -
NAC policy
14 -
Users
14 -
FortiManager v5.0
13 -
DNS filter
13 -
FortiDeceptor
12 -
Fabric connector
12 -
Port policy
12 -
FortiBridge
11 -
FortiRecorder
11 -
trunk
11 -
Traffic shaping profile
11 -
Authentication rule and scheme
11 -
FortiAnalyzer v5.0
10 -
FortiWeb v5.0
10 -
Fortinet Engage Partner Program
10 -
FortiGate v4.0 MR3
9 -
RMA Information and Announcements
9 -
Antivirus profile
9 -
Application signature
9 -
FortiCache
8 -
FortiToken Cloud
8 -
Packet capture
8 -
Vulnerability Management
8 -
4.0
7 -
4.0MR2
7 -
VoIP profile
7 -
FortiScan
6 -
FortiNDR
6 -
DoS policy
6 -
FortiCarrier
5 -
FortiTester
5 -
DLP profile
5 -
DLP sensor
5 -
Email filter profile
5 -
Protocol option
5 -
TACACS
5 -
Service
5 -
Cloud Management Security
5 -
3.6
4 -
FortiDirector
4 -
Internet service database
4 -
DLP Dictionary
4 -
Netflow
4 -
Replacement messages
4 -
SDN connector
4 -
Multicast routing
4 -
FortiDB
3 -
FortiHypervisor
3 -
FortiAI
3 -
Kerberos
3 -
Video Filter
3 -
File filter
3 -
Multicast policy
3 -
FortiEdge Cloud
3 -
FortiInsight
2 -
Schedule
2 -
ICAP profile
2 -
Zone
2 -
Lacework
2 -
FortiGuest
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Subscription Renewal Policy
1 -
FortiSASE
1 -
Virtual wire pair
1 -
FortiPresence
1 -
FortiEdge
1 -
FortiAIOps
1
| User | Count |
|---|---|
| 2841 | |
| 1436 | |
| 812 | |
| 802 | |
| 455 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2025 Fortinet, Inc. All Rights Reserved.