- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Support Forum
- Radius in serveur mode on five ssid with different...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Radius in serveur mode on five ssid with different acces group
My configuration:
FortiGate 200E Firmware 7.2.3
Access point FortiAP-231F X 20
Server windows 2022 Standard Role NPS (Radius)
I am looking for a configuration that allows the use of radius for the different SSID WIFI in "server radius" mode and not local.
We have 5 different SSID for wifi on each access point FortiAP-231F
We have created 5 different groups for the users of each SSID:
Group active directory security "Grp1" for SSID WIFI 1, "Grp2" for SSID WIFI 2, "Grp3" for SSID WIFI 3, "Grp4" for SSID WIFI 4, "Grp5" for SSID WIFI 5
The windows 2022 "NPS" Radius server communicates well with our FortiGate 200E firewall but it only works for one group:
The security group "Grp1" for SSID WIFI 1 in server radius mode works, but if I activate the "Grp2" for SSID WIFI 2, users of the "Grp1" and "Grp2" can connect to the SSID WIFI 1 and 2
We want users of the "Grp1" to be able to connect only to the SSID WIFI 1 and not to the two idem for the "Grp2".
The condition doesn’t work.
- Labels:
-
FortiGate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Yeap you can achieve this by using source attribute.
You need to create for each SSID an Radius policy filtering for source attribute criteria:
Vendor: Fortinet
Attribute ID: Fortinet SSID
Value(string): <SSID Name>
Fortigate as Radius client send the SSID NAME as attribute to the Radius Server in this case NPS. On a Radius Debug log on the server (or PCAP) you can verify what are the attribute that you receives for each SSID.
Article below explain how to filter for source attribute Called-Station-ID on Fortiauthenticator Raidus Server:
https://community.fortinet.com/t5/FortiAuthenticator/Technical-Tip-FortiAuthenticator-radius-profile...
So you need firstly to filter for the SSID source attribute criteria then validate the user and sending back the Radius attribute User Group Name "Grp1", "Grp2" etc.
User Group name is an attribute that is returned back from NPS radius server in order to match the group created on Fortigate:
config user group
edit "Group1"
set member "NPS"
config match
edit 1
set server-name "NPS"
set group-name "Grp1"
next
end
next
end
Additionally VSAs article that might also help you:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Fortinet-s-RADIUS-Dictionary-and-VSAs-late...
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Already done, it doesn’t work.
Article below explain how to filter for source attribute Called-Station-ID on Fortiauthenticator Raidus Server:
https://community.fortinet.com/t5/FortiAuthenticator/Technical-Tip-FortiAuthenticator-radius-profile...
No option on my Fortigate 200E maj 7.2.3
You need to create for each SSID an Radius policy filtering for source attribute criteria :
Vendor: Fortinet
Attribute ID: Fortinet SSID
Value(string): <SSID Name>
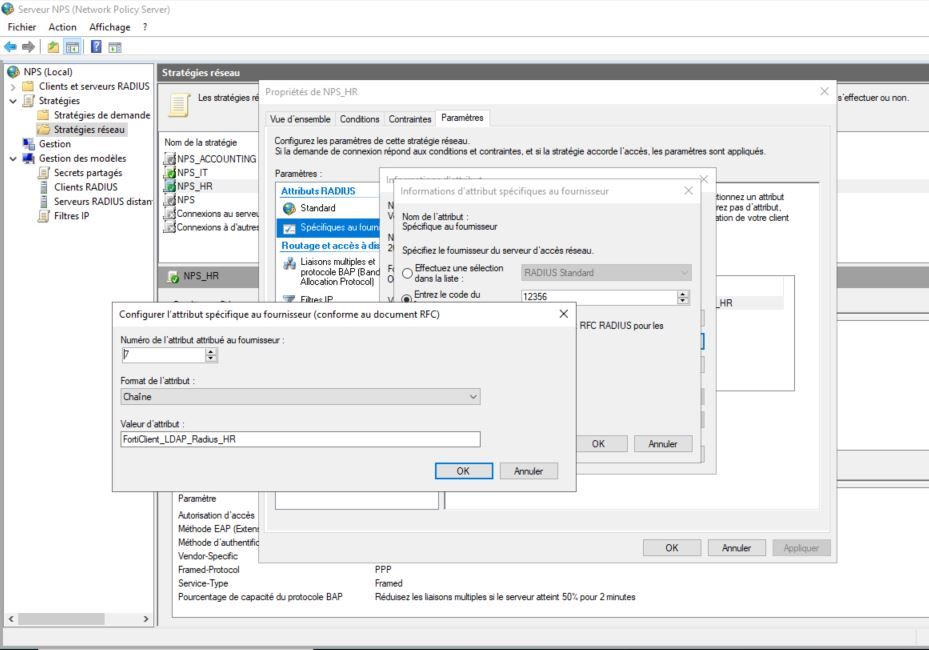
On the standard 2022 server (NPS role)
Supplier Specific tab -> Add (in supplier I don’t have Fortigate).
I add Vendor-Specifique :
Enter the supplier code : 12356
Yes, it is compliant
supplier code : 12356
Value: FortiClient_LDAP_Radius_HR
Attribute format : String
Attribute number assigned to supplier: 7
I tried with 6 too
See pj
La commande passée sur le Fortigate200E
config user group
edit "FortiClient_LDAP_Radius_HR"
Name of the active directory security group
set member "AD - Radius"
#Name of the radius server entered on the Fortigate200E box
config match
edit 1
set server-name "AD - Radius"
#Name of the radius server entered on the Fortigate200E box
set group-name "FortiClient_LDAP_Radius_HR"
next
end
next
end
Still the same problem, it work but the user from another security group radius can log on every ssid
-
FortiGate
11,167 -
FortiClient
2,297 -
FortiManager
937 -
FortiAnalyzer
709 -
5.2
687 -
5.4
638 -
FortiClient EMS
619 -
FortiSwitch
614 -
FortiAP
583 -
ipsec
488 -
6.0
416 -
SSL-VPN
414 -
FortiMail
388 -
5.6
362 -
FortiNAC
324 -
FortiWeb
272 -
6.2
251 -
FortiAuthenticator v5.5
234 -
SD-WAN
219 -
FortiAuthenticator
199 -
FortiGate-VM
168 -
FortiGuard
168 -
Firewall policy
155 -
5.0
152 -
6.4
128 -
FortiCloud Products
122 -
FortiSIEM
121 -
FortiToken
118 -
FortiGateCloud
113 -
High Availability
99 -
Wireless Controller
98 -
Customer Service
91 -
SAML
86 -
Routing
85 -
ZTNA
85 -
FortiProxy
81 -
Authentication
80 -
FortiADC
77 -
BGP
76 -
VLAN
76 -
DNS
75 -
Certificate
75 -
Fortivoice
73 -
FortiEDR
73 -
LDAP
70 -
RADIUS
69 -
FortiLink
64 -
SSO
63 -
NAT
59 -
FortiSandbox
57 -
Interface
57 -
Application control
55 -
FortiExtender
53 -
VDOM
52 -
4.0MR3
49 -
Virtual IP
49 -
Logging
45 -
FortiDNS
43 -
FortiPAM
42 -
SSL SSH inspection
42 -
Web profile
39 -
FortiGate v5.4
38 -
FortiSwitch v6.4
38 -
FortiConnect
36 -
Automation
36 -
FortiConverter
33 -
FortiWAN
32 -
API
32 -
Traffic shaping
29 -
FortiGate v5.2
28 -
FortiGate Cloud
28 -
Static route
28 -
SNMP
26 -
SSID
26 -
System settings
25 -
OSPF
24 -
FortiSwitch v6.2
23 -
FortiPortal
23 -
WAN optimization
23 -
Web application firewall profile
23 -
FortiMonitor
21 -
IP address management - IPAM
21 -
Security profile
20 -
Web rating
20 -
FortiSOAR
19 -
FortiAP profile
18 -
Admin
17 -
Intrusion prevention
17 -
FortiGate v5.0
16 -
FortiDDoS
16 -
Explicit proxy
16 -
IPS signature
16 -
FortiManager v4.0
15 -
NAC policy
15 -
Users
15 -
Traffic shaping policy
15 -
Proxy policy
15 -
FortiManager v5.0
14 -
FortiCASB
14 -
DNS filter
13 -
FortiDeceptor
12 -
Fabric connector
12 -
Port policy
12 -
FortiWeb v5.0
11 -
FortiBridge
11 -
trunk
11 -
Traffic shaping profile
11 -
Authentication rule and scheme
11 -
FortiAnalyzer v5.0
10 -
FortiRecorder
10 -
Fortinet Engage Partner Program
10 -
FortiGate v4.0 MR3
9 -
RMA Information and Announcements
9 -
Antivirus profile
9 -
Application signature
9 -
FortiCache
8 -
FortiToken Cloud
8 -
Packet capture
8 -
Vulnerability Management
8 -
4.0
7 -
4.0MR2
7 -
FortiNDR
7 -
VoIP profile
7 -
FortiScan
6 -
FortiTester
6 -
DoS policy
6 -
FortiCarrier
5 -
DLP profile
5 -
DLP sensor
5 -
Email filter profile
5 -
Protocol option
5 -
TACACS
5 -
Service
5 -
Cloud Management Security
5 -
3.6
4 -
FortiHypervisor
4 -
FortiDirector
4 -
Internet service database
4 -
DLP Dictionary
4 -
Netflow
4 -
Replacement messages
4 -
SDN connector
4 -
Multicast routing
4 -
FortiDB
3 -
FortiAI
3 -
Kerberos
3 -
Video Filter
3 -
File filter
3 -
Multicast policy
3 -
Zone
3 -
FortiEdge Cloud
3 -
FortiInsight
2 -
Schedule
2 -
ICAP profile
2 -
Virtual wire pair
2 -
Lacework
2 -
FortiGuest
2 -
FortiEdge
2 -
4.0MR1
1 -
FortiManager-VM
1 -
FortiCWP
1 -
Subscription Renewal Policy
1 -
FortiSASE
1 -
FortiPresence
1 -
FortiAIOps
1
| User | Count |
|---|---|
| 2912 | |
| 1451 | |
| 851 | |
| 826 | |
| 455 |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.