- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: How to read SAML Debug output
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
| Description |
This article describes how to read SAML logs with the output obtained from the SAML debugs. |
| Scope | FortiGate |
| Solution |
Use the output of the following debugs for SAML login as an example for the user:
diagnose debug reset
Once the user enters the credentials and tries to connect, the following outputs will be seen in the FortiGate. The request will come to the FortiGate, and FortiGate will redirect the Client to the IDP SSO URL with AuthnRequest (HTTP-Redirect).
IDP receives and validates AuthnRequest, then authenticates the client. Once the IDP authenticates, it will redirect the client to the SP to authorize the user.
The following is a redirection to the SAML IDP by FortiGate. This request is sent to the Client by the FortiGate.
Focus on the following fields from the log:
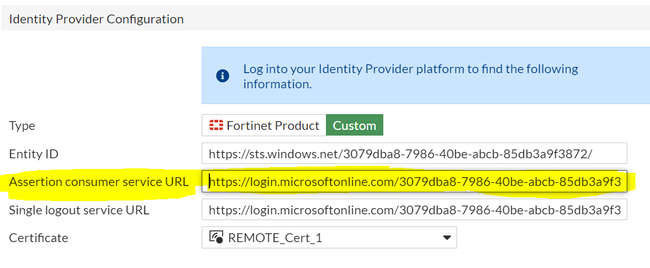
ID: _838F60F6BF4143F97B99446E866BFDDA <- This is the ID for this request. The complete authentication process will be identified with this ID.
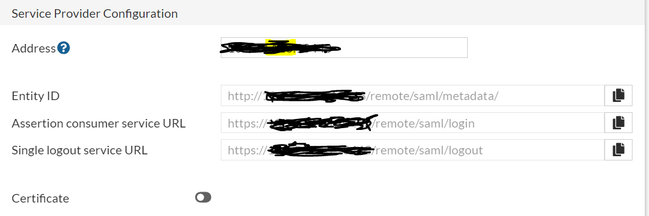
Issuer: http://10.5.24.116:10443/remote/saml/metadata/ <- This will be the SP URL that is sending the redirection towards IDP to the Client. This is configured in the SAML SP configuration's Entity ID.
This is located under: "User & Authentication" > "Single Sign On" > "Service Provider Configuration"
__samld_sp_create_auth_req [447]: SAML SP algo: 0 -> lasso=1. Binding Method: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST __samld_sp_create_auth_req [467]: saml2?SAMLRequest=hZJdb5swFIb%2FCvI9YLBLwEoiJWVokdoNN zHaTf9B38GMC56NfSmrHlosNmqxmhjvhmOYKHPM9O%2B5ub1ieYHa 2xpveSPQKeZ%2FgzoH v0EBD5BzExy081z7EOGcxBmOMTlllBHMSPUNRXXoIDT3C%2FXg%2F dmxNJXmXuhEid4aZ0Z gxtofF1QaNXDqYN2pDKfEIL0n7ZGUv9CD0%2FftCusuQYx9PpzZuP x9PKNo9S7o22k0K7BH n%2Fggo8H7jn6Tp9za4v3%2BRT2P9Qt0aK%2FvcsQ3H%2F73pZki2 JGOJxGWWTdmfoxShgC c%3D229ae47d0cee7bb9
SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML :2.0:assertion" ID IssueInstant="2023-10-03T14:30:39Z" Destination="https://login.microsofto SignType="0" SignMethod="0" ForceAuthn="false" IsPassive="false" Proto AssertionConsumerServiceURL="https://x.x.x.x:10443/remote/sa metadata/</saml:Issuer><samlp:NameIDPolicy Format="urn:oasis:nam xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" <lasso:Request><samlp:AuthnRequest ID="_838F60F6BF4 Destination="https://login.microsoftonline.com/3079 ForceAuthn="false" IsPassive="false" ProtocolBinding="ur AssertionConsumerServiceURL="https://x.x.x.x:10443/remote/saml/login"><sam <samlp:NameIDPolicy Format="urn:oasis:names:tc:SAML:1.1 </lasso:Request><lasso:RemoteProviderID>https://sts.win <lasso:MsgUrl>https://login.microsoftonline.com/3079d wEoiJWVokdoNNdkudjMZOLSW%2FJHZptv%2B%2FQxpu%2FZi3aVf SPQKeZ%2FgzoH1wmgUHeoN%2Bl6SsilwU%2BwbmlHSVKt9VVFafC XmXuhEid4aZ0ZvtBQakt6olOBVNXS8jFdVWcQUdxDzru%2Fi8mro o9S7o22k0K7BHso%2Bjhy93N30IZTq6SnCZZVrAMU0pSC8p4WFa9 GWWTdmfoxShgCC2lND%2BvLXAf1Hk7AUq3l0fffsftHw%3D%3D&a magic=229ae47d0cee7bb9</lasso:MsgRelayState><lasso 4143F97B99446E866BFDDA</lasso:RequestID></lasso:Lo
This is the response received from the IDP which is received by the Client and is forwarded to the FortiGate. Here, the SAML Authentication Statement and the SAML Attribute Statement can be seen.
The SAML Authentication Statement shows if the subject is authenticated using a provided authentication assertion method at a given time.
Destination="https://10.5.24.116:10443/remote/saml/login" <- Since this is the response from IDP, the destination will be the Assertion CS URL of the SP configured in FGT.
InResponseTo="_838F60F6BF4143F97B99446E866BFDDA" <- This is the ID which the IDP has sent the response for. This will be the ID field from the above request.
IssueInstant="2023-10-03T14:30:43.494Z" <- The time when the Response was sent by the IDP.
Issuer: https://sts.windows.net/3079dba8-7986-40be-abcb-85db3a9f3872/ <- This will be the Entitity ID of the IDP.
Certificate: This is the IDP certificate imported in the FortiGate. Match this Certificate if any Cert errors are encountered.
Recipient="https://x.x.x.x:10443/remote/saml/login" <- This will be same as the destination.
Audience: http://x.x.x.x:10443/remote/saml/metadata/ <- This will be the SP Entity ID.
Attribute Name & Attribute Value will be the attributes that are present in the IDP.
NotBefore="2023-10-03T14:25:43.316Z" NotOnOrAfter="2023-10-03T15:30:43.316Z" <- This is the assertion condition.
__samld_sp_login_resp [832]: IssueInstant="2023-10-03T14:30:43.496Z" Destination xmlns:samlp="urn:oasis:names https://sts.windows.net/3079dba8-5826-40be-abcb Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><A IssueInstant="2023-10-03T14:30:43.494Z" Version="2.0" xmlns="urn:oasis:n </Issuer><Signature xmlns=" <CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/ <Reference URI="#_91d40c9a-b665-42d1-bf93-0 <Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/> <Transform Algorithm= <DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/>< </Reference></SignedInfo><SignatureValue>G6C1yew577xFT yhDyOUfmKEGl68+9s/2zg+uzecVXKOPo6sd2SZuOYSea/8oCUrW8Z adCIZbHIM1bNYATe3puTlim97 57DDd7CRr/w==</SignatureValue><KeyInfo><X509Data><X509 sFADA0MTIwMAYDVQQDEylNaWNyb3NvZnQgQXp1cmUgRmVkZXJhdGVk AwBgNVBAMTKU1pY3Jvc29mdCBBenVyZSBGZWRlcmF0ZWQgU1NPIENl oFBgRv1zS4ukg/kg6PJZkrW4b79LpCBCNT9aXD6lt5wK8z9PHpM3fc 7BssYtL17XuXnmE5uPlrGAcWzUtDHtJhKum+FhdfEVDNCPMT33d1Dj 8WL1h/aDNVNyVfU5GmBe3hC9ZYAXq/vPJ9FBkINyMkRHIMwrNY9RwF MEPz8VHDdCePMswdbsdg/E1BNhNXja2VI/cXISpE3TEpx9owJy6qwB yibZmkeDbLRfPs7nHU8IhJxWq6PWTerxbdZIJTA1ITOrMgWO49xIwe c2MXVoyWusRAIr+7bFau3ap3dJkzy4lsyCtGvBde6M9SzYvjA/5vw3 </Signature><Subject><NameID Format="urn:oasis:names:tc:S <SubjectConfirmationMethod="urn:oasis:names:tc:SAML:2.0:cm: NotOnOrAfter="202 </SubjectConfirmation></Subject><Conditions <AudienceRestriction><Audience>http://x.x.x.x:10443/remote/saml/metadata/ </Audience></AudienceRestriction></Conditions><AttributeStatement><Attribute Name="http://sche </AttributeValue></Attribute <AttributeValue>096dba4e-b291-47ae-8cc7-437 Name="http://schemas.microsoft.com/identity/claims/displayname"><AttributeV Name="http://schemas.microsoft.com/identity/claims/identityprovider"><Att </AttributeValue></Attribute><Attribute Name="http: http://schemas.microsoft.com/ws/2008/06/identity/auth <Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/clai </Attribute><Attribute Name="http://schemas.xm </Attribute><Attribute Name="http://s <AttributeValue>xyz</AttributeValue></Attribute><Attribute Name=" <AttributeValue>abc@abc685gmail.onmicrosoft.com</AttributeV <AuthnStatement AuthnInstant="2023-10-02T10:54:34.349Z" SessionIndex="_91d40c9a-b665-4 urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClas
In the above Login Resp Body, the following is the Attribute Statement. An attribute statement asserts that a subject S has attribute A in namespace N with value(s) V.
<AttributeStatement><Attribute Name="http://sche <AttributeValue>3079dba8-7986-40be-abcb-85db3a9f3872</AttributeValue></Attribute <AttributeValue>096dba4e-b291-47ae-8cc7-437 <Attribute Name="http://schemas.microsoft.com/identity/claims/displayname"><AttributeV <Attribute Name="http://schemas.microsoft.com/identity/claims/identityprovider"><Att </AttributeValue></Attribute><Attribute Name="http: <AttributeValue>http://schemas.microsoft.com/ws/2008/06/identity/auth <Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/clai </AttributeValue></Attribute><Attribute Name="http://schemas.xm </AttributeValue></Attribute><Attribute Name="http://s <AttributeValue>abc</AttributeValue></Attribute><Attribute Name=" <AttributeValue>abc@abc685gmail.onmicrosoft.com</At <AttributeValue>abc@abcgmail.onmicrosoft.com</AttributeV
This is the Authentication Statement. An authentication statement asserts that a subject S is authenticated to the issuing system using method M at time T.
<AuthnStatement AuthnInstant="2023-10-02T10:54:34.349Z" SessionIndex="_91d40c9a-b665-4 <AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClas
Below are the attribute values that the IDP has sent:
<saml:NameID xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddre 'http://schemas.microsoft.com/identity/claims/tenantid' '3079dba8-7986-40be 'http://schemas.microsoft.com/identity/claims/objectidentifier' '096dba4e- 'http://schemas.microsoft.com/identity/claims/displayname' 'abc' 'http://schemas.microsoft.com/identity/claims/identityprovider' 'https://s 'http://schemas.microsoft.com/claims/authnmethodsreferences' 'http://schem 'http://schemas.microsoft.com/ws/2008/06/identity/claims/wids' 'b79fbf4d-3 'http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname' 'abc' 'http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname' 'xyz' 'http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name' 'abc@xyz.onmicrosoft.com' 'username' 'abc@xyz685gmail.onmicrosoft.com' <- This is the attribute added in FortiGate. This attribute will be expected from the IDP. samld_send_common_reply [122]: Attr: 11, 670, https://login.microsoftonline.com/ 3079dba8-7986-21ax-abcb-85db3a9f3872/sam juN5xZ7DoqO17krT%2F7a%2Fph%2FlxNTMWzHV2U88s gnB2U7M94QQUv0yIeX4DMp6hGK%2Fm6GJSLuUWIhRiB 7rjipxonxFqikZAe16qnI2EdpJOitjVNYlYSXGjcSIM B%2Fik7NDw%2BjwNld79Cz3FfbWx%2FLzYuMj7LJO3d f7n%2Fn1L4A&RelayState=magic%3D229ae47d0cee7bb9
Note: Stop the SAML debugging with the following command:
diagnose debug disable diagnose debug application samld 0
To collect the SAML logs from the user's browser, use SAML extensions:
Related articles: Technical Tip: How to fix crashing SAML daemon Technical Tip: A basic explanation of SAML authentication Technical Tip: Configuring SAML SSO login for FortiGate Admin Web GUI Access with JumpCloud acting a... Technical Tip: Set up SAML admin LDAP login on FortiGate (SP) with FortiAuthenticator (IDP) Technical Tip: Configuring FortiGate SSO Administrators with ADFS as SAML IdP Troubleshooting Tip: Admin authentication with SAML SSO breaks after upgrade to firmware 7.4.1 Technical Tip: Configure SAML SSO for WiFi SSID over Captive Portal with Azure AD as IdP |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Really good information.
SAML is a protocol that provides (from my perspective) more security than LDAP or Radius so it is being implemented more and more by customers.
For troubleshooting purposes it is important to know what means each SAML message/process. This makes easier to identify the problem.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.