- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiProxy
- Technical Tip: Bypassing WebSocket Secure (wss) co...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
| Description | This article describes a control to bypass a WebSocket Secure (wss) upgrade connection through FortiProxy. |
| Scope | FortiProxy. |
| Solution |
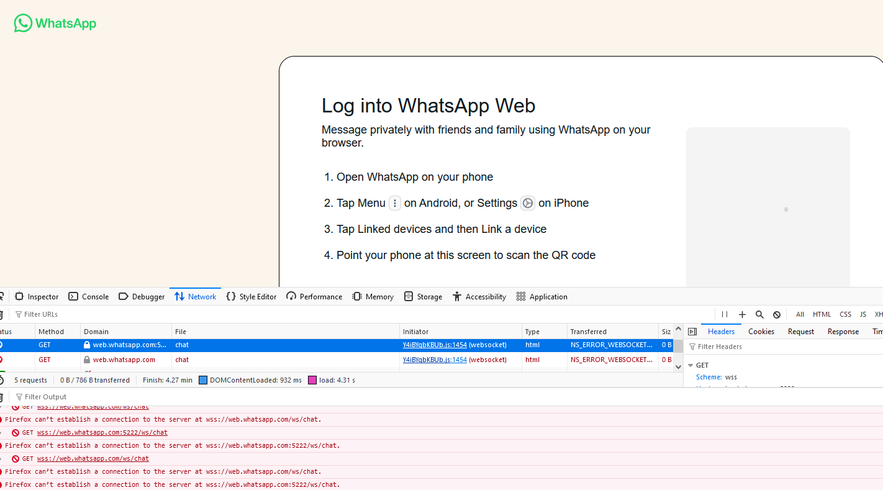
Proxy user requests to access a web socket application with a connection error shown on web developer tools output.
Example: Firefox cannot establish a connection to the server at wss://web.whatsapp.com:5222/ws/chat?ED=CAIICA
Perform a WAD debug to trace the traffic, the issue can be identified with a switching protocol error.
GET /ws/chat?ED=CAIICA HTTP/1.1 ... [W][p:1067][s:80313340][r:3713] wad_http_urlfilter_check :438 Switch Protocol Block.
In this scenario, it is necessary to ensure a bypass connection when switching protocol has been enabled under the proxy protocol profile options.
config firewall profile-protocol-options |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.