- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiManager
- Technical Tip: Certificate Template with SCEP enro...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article describes how to configure Certificate Template with SCEP enrollment on FortiManager, using a FortiAuthenticator as an external Certificate Authority.
Scope
FortiManager 6.4 or above.
Solution
Create an external certificate template using FortiAuthenticator.
In FortiAuthenticator, enable SCEP under the relevant interface/s, Network -> Interface.
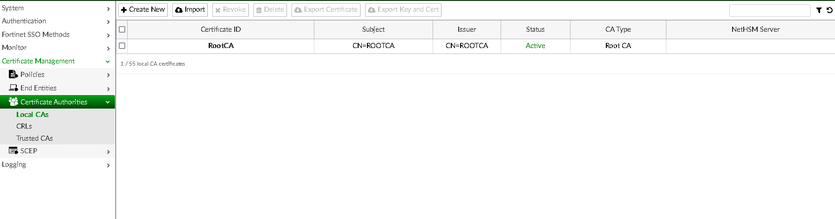
Configure a local CA under Certificate Management -> Certificate Authorities -> Local CAs.
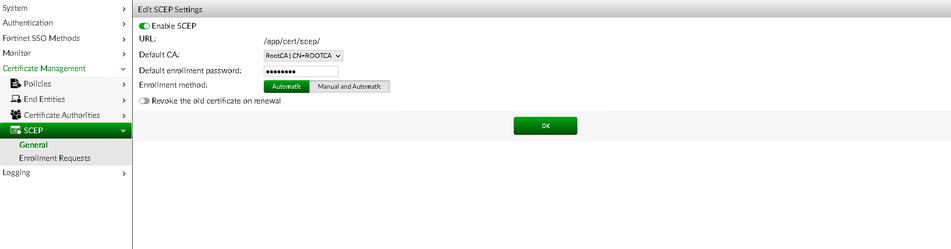
Select the CA from step b) under the SCEP settings under Certificate Management -> SCEP -> General.
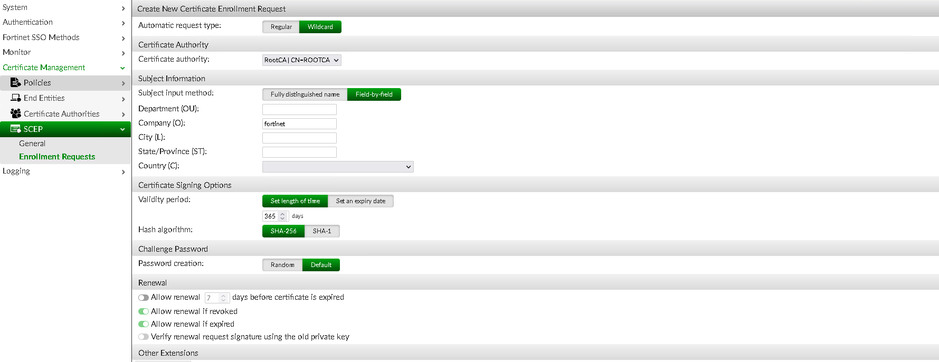
Create new Automatic 'Wildcard' Enrolment Request and fill in the required certificate information under Certificate Management -> SCEP -> Enrollment Requests.
In this example, the 'Company' field is set to ‘fortinet’, matching the 'Organization' field on the FortiManager side.
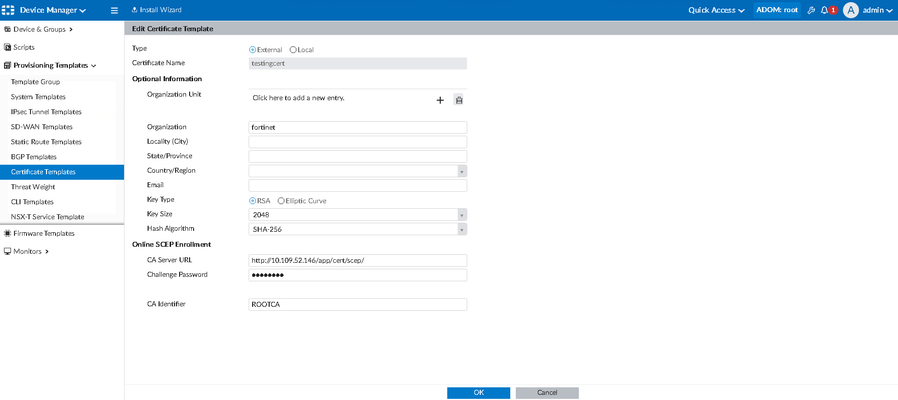
In FortiManager, create new Certificate Template under Device Manager -> Provisioning Templates -> Certificate Templates -> Create New.
CA Identifier is ROOTCA and Organization 'fortinet' in order to match the wildcard enrollment request on FortiAuthenticator.
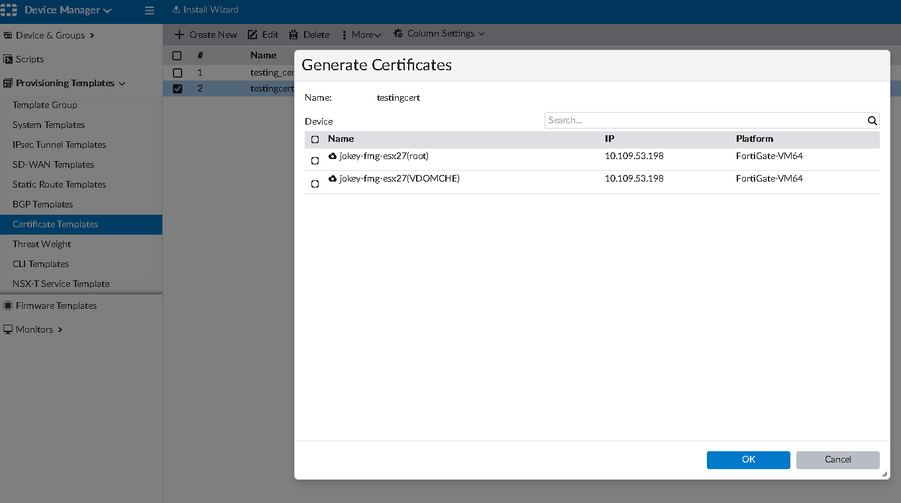
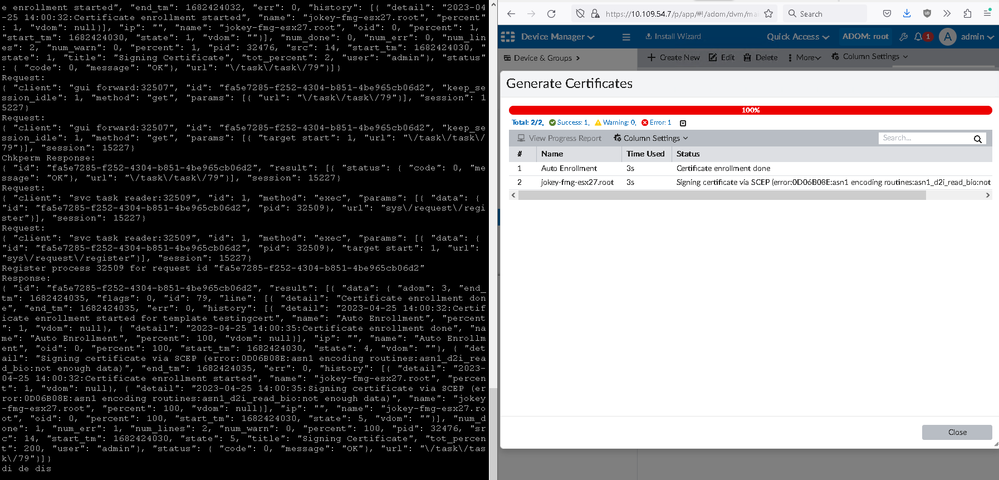
To test, generate a new certificate for one of the devices under Device Manager -> Provisioning Templates -> Certificate Templates -> selecting 'testingcert' -> More -> Generate.
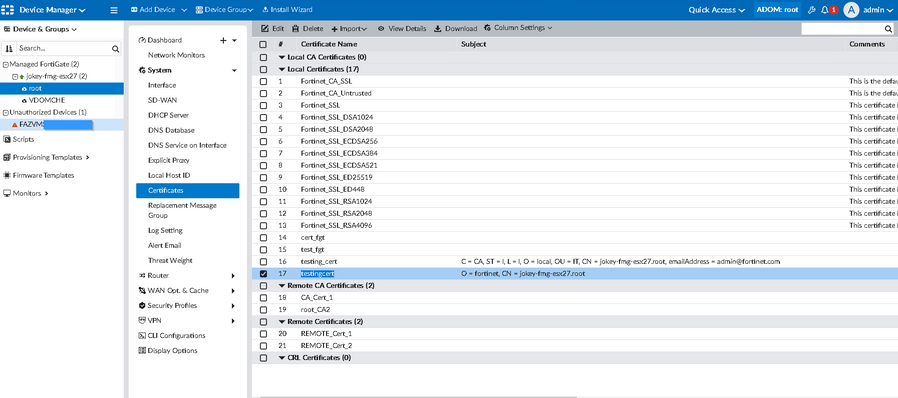
Check the newly created certificate on the device under Device Manager -> Device & Groups -> Managed FortiGate -> NAME(root) -> System -> Certificates.
It has a name matching the template name and the subject is always CN = <devicename>.<vdomname>. In this example - CN=jokey-fmg-esx27.root
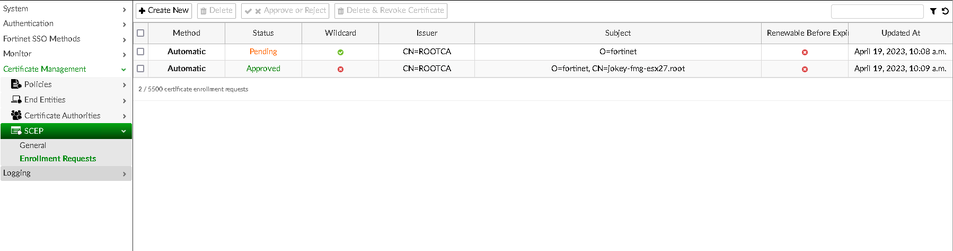
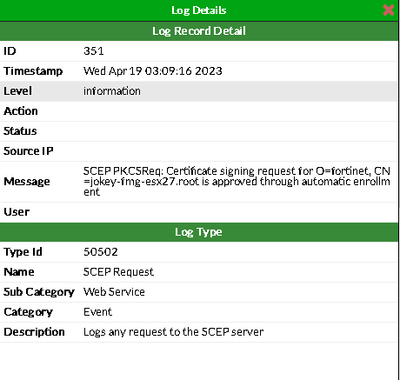
The approved request can be seen on the FortiAuthenticator side under Certificate Management -> SCEP -> Enrollment Requests.
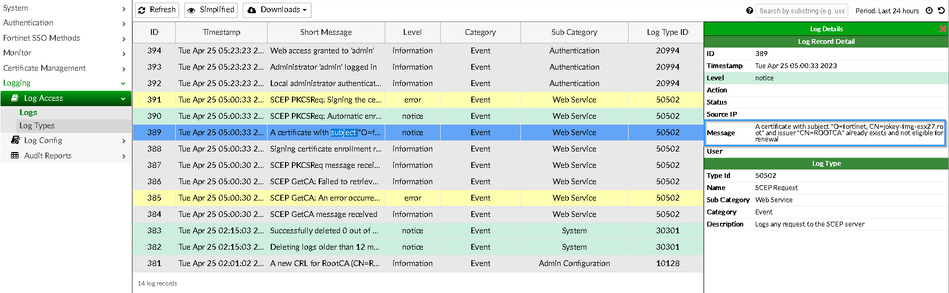
The same information is also available in the FortiAuthenticator logs under Logging -> Log Access -> Logs.
Troubleshooting:
For troubleshooting the SCEP enrollment process, it is possible to temporarily set the FortiAuthenticator in HTTP mode, and then, use packet capture to view the communication between FortiManager and FortiAuthenticator.
Use the packet capturing options in the FortiManager GUI under System settings -> Network Interfaces -> Packet capture.
Or under CLI:
# diagnose sniffer packet any "host x.x.x.x and port 80" 3 0 a
The following debug commands from the FortiManager could provide additional information:
# diag deb application securityconsole 255
# diag debug service sys 255
# diag debug service task 255
# diag debug enable
After the test:
# diag debug disable
# diag debug reset
Error example:
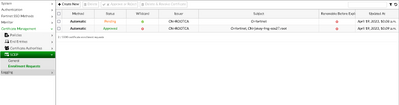
More details on the error message can be found in FortiManager Task Monitor under System Settings -> Task Monitor.
View also the FortiAuthenticator logs under Log Access -> Logs.
In this case, a certificate with subject 'O=fortinet, CN=jokey-fmg-esx27.root' and issuer 'CN=ROOTCA' already exists and is not eligible for renewal.
Related documents:
Creating a local CA on FortiAuthenticator
Technical Tip: Enabling the self-service portal for certificate enrollment and password changes
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.