- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: VXLAN multiple remote-ip per VNI us...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article describes how to configure VXLAN over IPsec for multiple remote-ip per VNI using a loopback interface.
Scope
FortiGate.
Solution
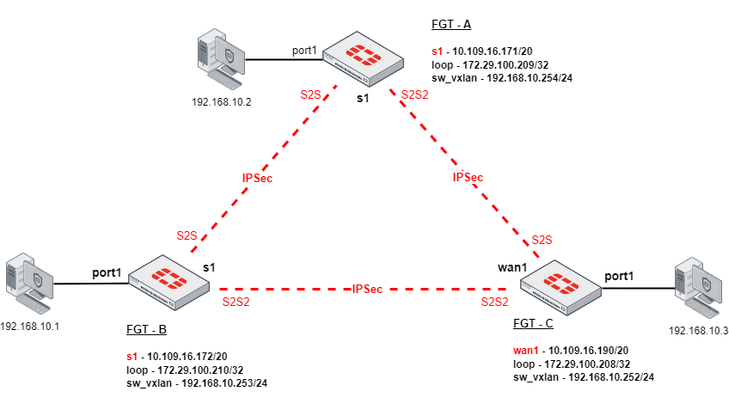
Diagram:
Use below CLI commands:
'FGT-A'
config system interface
edit "loop"
set vdom "root"
set ip 172.29.100.209 255.255.255.255
set allowaccess ping
set type loopback
next
end
config system vxlan
edit "vni240"
set interface "loop"
set vni 240
set remote-ip "172.29.100.210" "172.29.100.208"
next
end
config system switch-interface
edit "sw_vxlan"
set vdom "root"
set member "port1" "vni240"
next
end
config vpn ipsec phase1-interface
edit "S2S"
set interface "s1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.172
set psksecret password
next
edit "S2S2"
set interface "s1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.190
set psksecret password
next
end
config vpn ipsec phase2-interface
edit "S2S"
set phase1name "S2S"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
edit "S2S2"
set phase1name "S2S2"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
end
config router static
edit 2
set dst 172.29.100.210 255.255.255.255
set device "S2S"
next
edit 3
set dst 172.29.100.208 255.255.255.255
set device "S2S2"
next
end
config firewall policy
edit 1
set name "Loopback to IPSec"
set srcintf "loop"
set dstintf "S2S" "S2S2"
set action accept
set srcaddr "all"
set dstaddr "all"
set schedule "always"
set service "ALL"
next
edit 2
set name "IPSec to Loopback"
set srcintf "S2S" "S2S2"
set dstintf "loop"
set action accept
set srcaddr "all"
set dstaddr "all"
set schedule "always"
set service "ALL"
next
end
'FGT-B'
config system interface
edit "loop"
set vdom "root"
set ip 172.29.100.210 255.255.255.255
set allowaccess ping
set type loopback
next
end
config system vxlan
edit "vni240"
set interface "loop"
set vni 240
set remote-ip "172.29.100.209" "172.29.100.208"
next
end
config system switch-interface
edit "sw_vxlan"
set vdom "root"
set member "port1" "vni240"
next
end
config vpn ipsec phase1-interface
edit "S2S"
set interface "s1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.171
set psksecret password
next
edit "S2S2"
set interface "s1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.190
set psksecret password
next
end
config vpn ipsec phase2-interface
edit "S2S"
set phase1name "S2S"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
edit "S2S2"
set phase1name "S2S2"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
end
config router static
edit 2
set dst 172.29.100.209 255.255.255.255
set device "S2S"
next
edit 3
set dst 172.29.100.208 255.255.255.255
set device "S2S2"
next
end
config firewall policy
edit 1
set name "Loopback to IPSec"
set srcintf "loop"
set dstintf "S2S" "S2S2"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set name "IPSec to Loopback"
set srcintf "S2S" "S2S2"
set dstintf "loop"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
'FGT-C'
config system interface
edit "loop"
set vdom "root"
set ip 172.29.100.208 255.255.255.255
set allowaccess ping
set type loopback
next
end
config system vxlan
edit "vni240"
set interface "loop"
set vni 240
set remote-ip "172.29.100.209" "172.29.100.210"
next
end
config system switch-interface
edit "sw_vxlan"
set vdom "root"
set member "port1" "vni240"
next
end
config vpn ipsec phase1-interface
edit "S2S"
set interface "wan1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.171
set psksecret password
next
edit "S2S2"
set interface "wan1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set remote-gw 10.109.16.172
set psksecret password
next
end
config vpn ipsec phase2-interface
edit "S2S"
set phase1name "S2S"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
edit "S2S2"
set phase1name "S2S2"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256
set auto-negotiate enable
next
end
config router static
edit 2
set dst 172.29.100.209 255.255.255.255
set device "S2S"
next
edit 3
set dst 172.29.100.210 255.255.255.255
set device "S2S2"
next
end
config firewall policy
edit 1
set name "Loopback to IPSec"
set srcintf "loop"
set dstintf "S2S" "S2S2"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set name "IPSec to Loopback"
set srcintf "S2S" "S2S2"
set dstintf "loop"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2025 Fortinet, Inc. All Rights Reserved.