- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: Redundant IPSEC Tunnel using single...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
| Description |
This article describes one of the methods to attain partial redundancy when one FortiGate has a single WAN connection and the other FortiGate has two or more WAN (ISPs) connections. |
| Scope | Site-to-Site IPSEC VPN, Static Route. |
| Solution |
Create separate IPSEC tunnel interfaces corresponding to each WAN connection on the peer end.
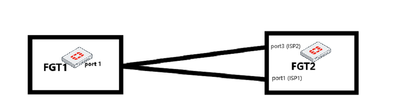
Representation:
Note: It is necessary for the FortiGate with two WAN connections that both default routes for its WAN interfaces are active. The same distance needs to be set on its metric: Dual internet connections
Tunnel corresponding to ISP2 on peer FGT1:
On FGT1:
# config vpn ipsec phase1-interface edit "to-ISP1" set interface "port1" set mode aggressive set peertype any set net-device disable set proposal aes128-sha256 set comments "VPN: to-ISP1 (Created by VPN wizard)" set dhgrp 2 set remote-gw 10.47.2.106 set psksecret ENC xxxxxx
Tunnel corresponding to ISP2 on peer FGT2:
config vpn ipsec phase1-interface edit "to-ISP2" set interface "port1" set mode aggressive set peertype any set net-device disable set proposal aes128-sha256 set comments "VPN: to-ISP2 (Created by VPN wizard)" set dhgrp 2 set nattraversal disable set remote-gw 10.47.18.106 set psksecret ENC xxxxxxxxxx
Note: Phase 2 and Firewall policies are configured accordingly.
Note: The config below explains the route to the same specific destination on peer FGT2, but the ISP-2 tunnel static route is configured with an increase in the priority value, which means this tunnel will act as a secondary route.
config router static edit 7 set dst 10.232.0.0 255.255.0.0 set device "to-ISP1" set priority 10 ->Priority value is 10 (default value) next edit 8 set dst 10.232.0.0 255.255.0.0 set priority 20 <----- Priority value is set to '20' which is higher than the default value '10'. set device "to-ISP2"
Configuration on FGT2: (This is the FortiGate with two or more ISPs).
config vpn ipsec phase1-interface edit "ISP1 tunnel" set interface "port1" set mode aggressive set peertype any set net-device disable set proposal aes128-sha256 set dhgrp 2 set remote-gw 10.47.19.94 set psksecret ENC xxxxxxx
config vpn ipsec phase1-interface edit "ISP2 tunnel" set interface "port3" set mode aggressive set peertype any set net-device disable set proposal aes128-sha256 set dhgrp 2 set nattraversal disable set remote-gw 10.47.19.94 set psksecret ENC xxxxxxx
Similarly, firewall policies and phase2 are configured accordingly. Static routes are to be created for each tunnel as configured on FGT1,
edit 7 set device "ISP1 tunnel" set dst 10.213.0.0 255.255.0.0 set priority 10 ->Priority value is 10 (default value) next edit 5 set priority 20 <----- To be treated as a secondary tunnel. set device "ISP2 tunnel" set dst 10.213.0.0 255.255.0.0 next
Note: On FGT1 and FGT2 it will show both the tunnels to be active, but only the primary tunnel will be handling the traffic as it has a default priority '10', also only when the primary tunnel fail,s the traffic will be handled by the secondary tunnel.
Related articles: Technical Tip: Routing behavior depending on distance and priority for static routes, and Policy Bas... Technical Tip: How to configure VPN Site to Site between FortiGates (Using VPN Setup Wizard) |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.