- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Blogs
- Other ways to protect your cloud-native applicatio...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
While AWS provides a strong foundation of native security tools, organizations often seek additional layers of protection to meet specific compliance, visibility, or threat prevention needs. This is where FortiGate and FortiWeb solutions come into play. FortiGate is Fortinet’s flagship Next-Generation Firewall (NGFW) solution, designed to provide comprehensive, intelligent, and high-performance security for network whether on-premises, in the cloud, or across hybrid environments like AWS, offers advanced threat protection, secure VPN access, and deep traffic inspection, making it ideal for securing VPCs and hybrid cloud environments, for this scenario securing network traffic to and from fargate tasks by inspecting traffic at the VPC level, enforcing segmentation, and blocking malicious activity through deep packet inspection and threat intelligence. Meanwhile, FortiWeb is a specialized web application firewall (WAF) designed to protect web applications such as Fargate-hosted APIs and web services or applications from known and unknown threats, including OWASP Top 10 vulnerabilities, bot attacks, and zero-day exploits. Both solutions integrate seamlessly with AWS infrastructure, offering auto-scaling, centralized management, and support for automation via AWS CloudFormation and Terraform. By incorporating FortiGate and FortiWeb into your cloud-native architecture, you can significantly enhance your security posture and ensure consistent protection across your workloads.
This article is the initial part of a broader blog series focused on securing diverse workloads in AWS using Fortinet solutions. Each post in the series explores how FortiGate and FortiWeb can be applied to different AWS services and architectures from traditional EC2 instances to serverless functions (lambda) and containers (ECS and Fargate). Whether you're running microservices on Fargate, APIs on Lambda, or Kubernetes clusters on EKS, this series provides practical insights and architectural guidance to help you build a consistent and resilient security posture across your cloud environment.
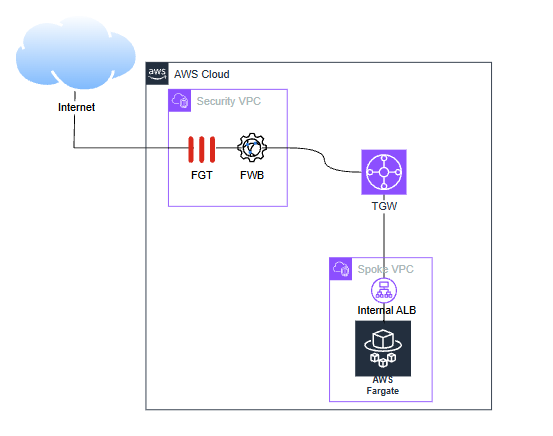
The following diagrams are the proposed infrastructure to completely protect your ECS fargate application
Use case 1
This diagram illustrates the recommended security architecture for applications that include file upload functionality. To ensure robust protection against potential threats, it is advised to deploy a FortiGate firewall at the network perimeter, positioned in front of the internet-facing interface. This setup acts as the first line of defense, including deep inspection of uploaded files, preventing attacks using file-based exploits targeted to application servers or containers, filtering and inspecting incoming traffic before it reaches the FortiWeb web application firewall. FortiWeb then provides specialized protection for web applications, to safeguard against web-based attacks such as malware injection, cross-site scripting (XSS), botnet protection and SQL injection. Together, FortiGate and FortiWeb form a layered security approach that significantly enhances the resilience of applications handling file uploads.
Use case 2
Below diagram presents a use case focused on securing both outbound and inbound traffic in a containerized environment using AWS Fargate. For outbound traffic originating from Fargate containers to the internet, FortiGate is deployed to provide advanced threat protection, traffic filtering, and policy enforcement, ensuring that only safe and authorized communications are allowed to specific URLs. Simultaneously, for inbound traffic targeting web applications, FortiWeb is positioned to deliver specialized web application firewall (WAF) capabilities. It inspects and protects against common web threats as said earlier such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. This dual-layered approach ensures comprehensive security coverage for both egress and ingress traffic in modern cloud-native application architectures.
The previously discussed use cases are all built upon a foundational architecture that aligns with industry best practices for securing modern applications. This approach emphasizes layered security, combining FortiGate for network-level protection and FortiWeb for application-layer defense. By following this model, organizations can significantly reduce their exposure to both known and emerging threats.
The following steps are for reference only:
- Deploy your Fargate application: Creating an application using AWS Fargate involves several steps, typically within the context of Amazon ECS (Elastic Container Service) or Amazon EKS (Elastic Kubernetes Service). Here's a high-level overview of the steps using Amazon ECS with Fargate, which is the most common approach:
- Develop your application and containerize it using Docker.
- Clone the example repo using github desktop or via cli git clone https://github.com/docker/welcome-to-docker
- Open in Visual Studio Code and modify index.html and scr/App.js files
- Develop your application and containerize it using Docker.
- Now build your tailored image using below command:
docker build -t welcome-to-docker .
- Next run it and check the frontend application using below command:
docker run -d -p 8088:3000 --name welcome-to-docker welcome-to-docker
- Push the image to a container registry like Amazon Elastic Container Registry (ECR)
- Get credentials for temporary AdministratorAccess
- Copy Values the access key and secret access key to configure later
- Create a repository
- Use on your local machine the following command: aws configure and paste the values as require the configure command
- Next, use the following command:
aws ecr get-login-password --region us-east-1 | docker login --username AWS --password-stdin XXXXXXXXXXXX.dkr.ecr.us-east-1.amazonaws.com
- Push the image you have created before, using this command:
docker images
docker tag <tag-id> XXXXXXXXXXXX.dkr.ecr.us-east-1.amazonaws.com/fargate-test-repo:version1
docker push XXXXXXXXXXXX.dkr.ecr.us-east-1.amazonaws.com/fargate-test-repo:version1
- Create an ECS cluster and create a Fargate ECS application
- Create an ECS Cluster
- Create a Task Role
- Create a Task Definition
Set Linux/X86_64
Set CPU = .25 vCPU and .5 GB to Memory
Use ecsTaskExecutionRole
- Use image URI XXXXXXXXXXXX.dkr.ecr.us-east-1.amazonaws.com/fargate-test-repo:version1 where XXXXXXXXXX must be replaced by your own account number
Use container port 3000
- Create security group (named DemoAppECS-sg) allowing TCP 3000 traffic for inbound and all traffic for outbound
- Create a Public service application
- Set the VPC and public subnets, segurity group created previously and turn ON public IP
- Test Application on your browser (this is public for application checking only, later will be deleted)
- Create a private service application
- Set the VPC and private subnets, segurity group created previously and turn OFF public IP (for this step you must warranty internet access to private subnets)
- After successful deployment, gather the IP of created container
- Deploy an application load balancer within VPC and private subnets
- Create an internal ALB and target group
Note: In some cases if customer doesn’t have FortiWeb VM deployed in your AWS environment you can strengthen your cloud security with Fortinet managed rules, for more information please check below links:
- Managed Rules for AWS WAF
- Protect Your Web Applications and APIs
- Strengthen Your Cloud Security With Managed Rules
- Register target IP gathered from previous step and click on “include as pending below”
- Come back to ALB page wizard and set the previously created target group
- Wait until target group becomes healthy
- Gather DNS name of application load balancer
- Open your FortiWeb console and register the new Fargate application load balancer DNS name on a new server pool
- Check connectivity from Fortiweb to gathered container IP
- Check connectivity from Fortiweb to load balancer DNS as well
- Create a server policy changing port number if desired
- Set a proper web protection profile according to application and security needs and select from policy
- Create a new fargate application service but now selecting all private subnets and without public IP, and associating the created load balancer for new containers being registered automatically on target group
- Create a new task definition now pointing to private subnets of your desired VPC
- From FortiGate create a VIP for external Fortiweb IP using port TCP 8081
- Create VIP for Fortiweb
- Create Firewall Rule for FortiWeb public access through FortiGate
- Test your application from browser
- Check traffic logs on FortiGate and FortiWeb consoles to ensure traffic is being inspected
- FortiGate traffic logs
- FortiWeb attack logs
- Do some Tunning on FortiWeb console according to your application behavior (if needed)
- Go Live changing your application DNS pointing to FortiGate public IP address.
- Delete Fargate public service created on previous step
Takeaways:
- Layered Security Architecture is Essential
Deploying FortiGate and FortiWeb in tandem provides a comprehensive security posture:
- FortiGate acts as the first line of defense, filtering and inspecting both inbound and outbound traffic at the network level.
- FortiWeb offers deep application-layer protection, especially critical for features like file uploads and web interfaces.
- Cloud-Native Environments Require Tailored Protection:
In containerized environments like AWS Fargate, it's crucial to:
- Secure outbound traffic from containers using FortiGate to prevent data exfiltration or malicious communication.
- Protect inbound application traffic with FortiWeb to mitigate layer 7 web-based threats.
- Follow Best Practices and Official Guidance:
- Please note that this blog outlines several design options intended solely for validation and conceptual understanding. These examples are not meant for direct use in production environments. For real-world deployments, we strongly recommend that customers engage with our cloud consulting services team to ensure proper design, configuration, and security alignment with organizational requirements and best practices. For more information you can check out the link below link:
https://www.fortinet.com/resources/security-consulting-services
Referencies:
AWS Fargate: https://aws.amazon.com/es/blogs/compute/building-deploying-and-operating-containerized-applications-...
AWS ECR: https://docs.aws.amazon.com/AmazonECR/latest/userguide/repository-create.html
AWS Image push: https://docs.aws.amazon.com/AmazonECR/latest/userguide/image-push.html
FortiWeb admin guide: https://docs.fortinet.com/document/fortiweb/7.4.8/administration-guide/60895/introduction
FortiGate admin guide: https://docs.fortinet.com/document/fortigate/7.4.8/administration-guide/954635/getting-started
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.