- Support Forum
- Knowledge Base
- Customer Service
- Internal Article Nominations
- FortiGate
- FortiClient
- FortiADC
- FortiAIOps
- FortiAnalyzer
- FortiAP
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCare Services
- FortiCarrier
- FortiCASB
- FortiConverter
- FortiCNP
- FortiDAST
- FortiData
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDLP
- FortiDeceptor
- FortiDevice
- FortiDevSec
- FortiDirector
- FortiEdgeCloud
- FortiEDR
- FortiEndpoint
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiGuest
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPhish
- FortiPortal
- FortiPresence
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSRA
- FortiSandbox
- FortiSASE
- FortiSASE Sovereign
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- FortiAppSec Cloud
- Lacework
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiSOAR
- Technical Tip: FortiDeceptor Content Pack
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on
08-16-2021
06:30 AM
Edited on
10-07-2025
08:18 AM
By
![]() Stephen_G
Stephen_G
Description
This article describes the FortiDeceptor Content Pack.
Scope
FortiDeceptor.
Solution
This content pack enables users to integrate with FortiDeceptor by providing a good default mapping for SysLog Ingestion of FortiDeceptor alerts, changes in default modules to accommodate event information, use case playbooks and more.
Based on deception technology, FortiDeceptor complements an organization’s existing breach protection strategy. It is designed to deceive, expose and eliminate external and internal threats early in the attack kill chain before any significant damage occurs. Integration with FortiSOAR allows to automate the response to alerts received from FortiDeceptor, ensuring a quick co-ordinated response action across various protection tools like FortiEDR, FortiNAC, FortiGate and FortiClient EMS, while getting information from users, Active Directory, FSR Asset inventory and other sources.
Inside the content pack:
- Ingestion Playbooks for fetching alerts from FortiDeceptor, via SysLog
- Default mapping within FortiDeceptor alert meta data and FortiSOAR alert fields
- Use Case Playbook - Lateral Movement Investigation and Response
- Use Case Playbook - VPN Breach Detection and Response
Required:
- Base IR Content Pack - Incident Response Content Pack 7.0.1.
- Configuring FortiSOAR SysLog Connector with FortiDeceptor instance's SysLog configurations.
Integrations used:
FortiEDR, FortiNAC, FortiGate, FortiClient EMS, Active Directory, SysLog
Solution summary:
Upon installation of this content pack and activation of the playbooks, alerts from FortiDeceptor will start arriving via syslog. Once alerts are ingested, FortiSOAR indicator extraction and enrichment workflows will auto-trigger and extract-enrich all the relevant observables from the FDC alert data, like Source IP, Destination IP, User Details etc. All the necessary correlations with existing indicators, assets, user data is also made to present a good informative alert for the analyst to investigate. The alert is also tagged with #FortiDeceptor tags and the severity is raised depending on the enrichment workflow results.
A very common use case that FortiDeceptor users use the product for is to detect Lateral Movement and VPN Breach Detection using deception lures for attackers. There are out-of-the-box use case playbooks provided as part of this content pack that to investigate and respond to these type of alert detections from FortiDeceptor.
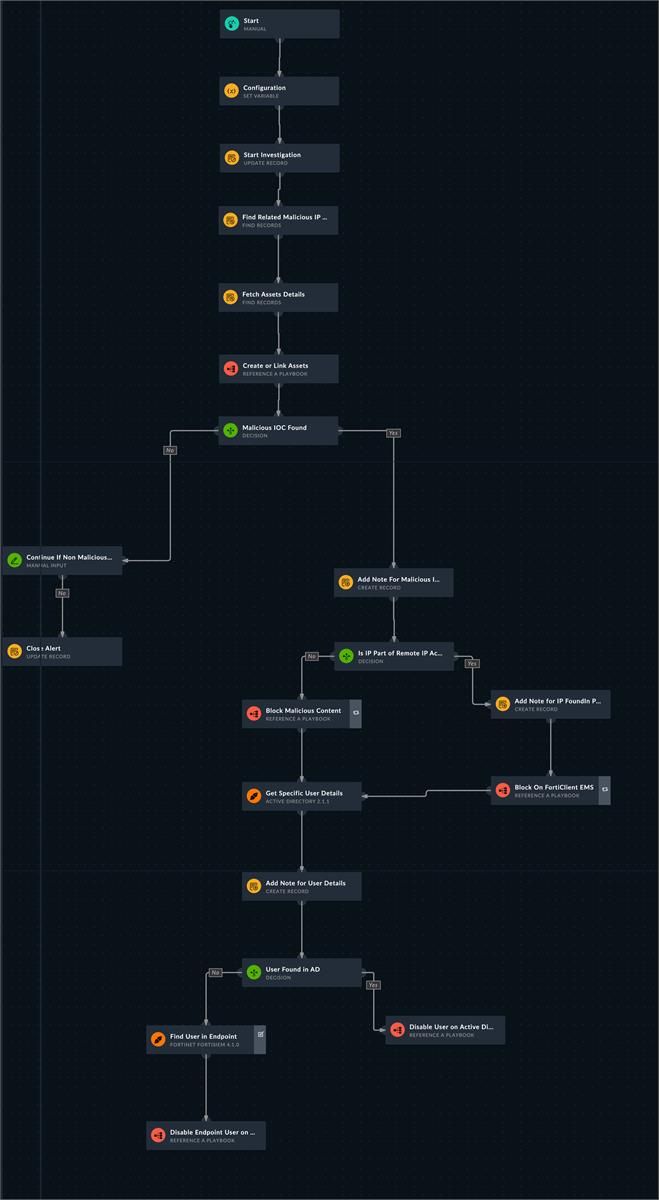
Lateral movement use case workflow:
- Ingest Demo Alert (SysLog)
- Auto Extract Decoy Details (under Destination IP)
- Auto Extract Attacker IP Details (Under SourceIP or AttackerIP) - tag it as Malicious
- Auto-Extract User Information (the username on the FDC alert can originate from a deception lure that does not exist in AD; if the username in the alert does not exist in AD, obtain the username from the endpoint that attacks the decoy. For example, a deception SSH lure to access a decoy will not be in AD; therefore, obtain the logon username on the infected endpoint and disable the corresponding account in AD.)
- Auto Extract Details of Decoy Asset - Pull details from FSR Asset DB (e.g. HostName)
- Initiate Block of AttackerIP in FortiEDR, FortiNAC, FortiGate
- Search User In Active Directory (AD)
- If User found, Disable in AD
- If User Not Found, then Notify IT teams about the same
VPN Breach Use Case Workflow:
- Ingest Demo Alert (SysLog)
- Auto Extract Decoy Details (under Destination IP)
- Auto Extract Attacker IP Details (Under SourceIP or AttackerIP) - tag it as Malicious
- Auto Extract User Information
- Playbook has a list of VPN Pool IPs available (configurable)
- Search for the AttackerIP in the VPN Pool. If found, block the same in FortiClient EMS(Asset details can be extracted from FSR Asset DB where records against each VPN Pool IP is present)
- Most of the time, the username for VPN access is the AD username; therefore, in addition to blocking on FortiClient EMS, block the compromised username in AD to prevent the attacker from accessing additional resources.
- If not found in VPN Pool, ask the User whether to block AttackerIP in FortiNAC, FortiEDR, and FortiGates.
- If Yes, block the same.
Playbook Screenshots:
 AKJTDpcDQ6uDzcODzcRl_FDC_Playbook-L.jpg
AKJTDpcDQ6uDzcODzcRl_FDC_Playbook-L.jpg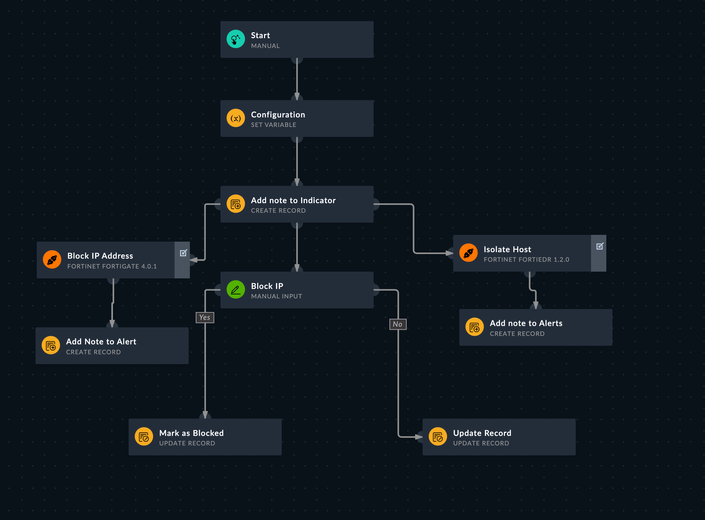 MRZ838DXSsqS4dJIaQEK_Screenshot 2021-08-16 at 6.35.12 PM.png
MRZ838DXSsqS4dJIaQEK_Screenshot 2021-08-16 at 6.35.12 PM.png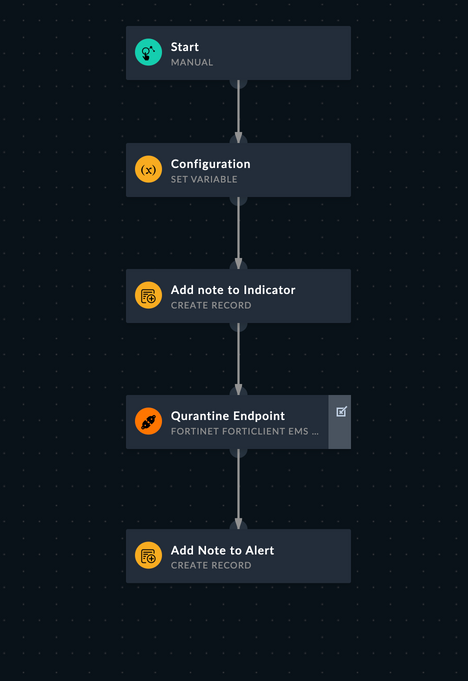 iAAAFAepTE6umKBWJ1DF_Screenshot 2021-08-16 at 6.37.16 PM.png
iAAAFAepTE6umKBWJ1DF_Screenshot 2021-08-16 at 6.37.16 PM.pngHow to install the content pack:
- Ensure the base IR Content Pack is installed.
- To install this add-on content pack, go to Settings -> Configuration Import.
- Unzip the attached file, upload (JSON) and initiate the guided Import Process.
- Review import artifacts and import the pack.
Video demonstration:
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2026 Fortinet, Inc. All Rights Reserved.