- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiNAC
- Technical Tip: SSID/AP check and Multihome detecti...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article describes the options in FortiNAC endpoint compliance configuration that allows administrators to Restrict Host connections to only whitelisted SSIDs/APs and additionally check for Dual Homes connections when there are multiple connected adapters on the same host.
Scope
FortiNAC.
Solution
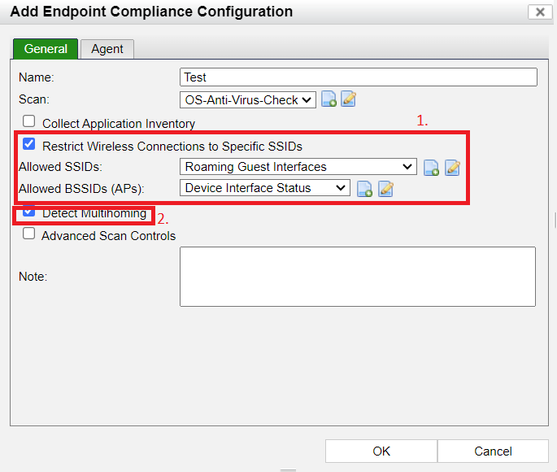
- Restrict Wireless Connections to Specific SSIDs.
Go to Policy&Object -> Endpoint Compliance -> Configuration.
When a host matches an Endpoint compliance policy where the configuration has the option 'Restrict Wireless Connections to Specific SSIDs' enabled, FortiNAC will check if the host is connected to an SSID/AP specified in the Group of allowed SSID and access points.
SSID information can be collected from sources such as the persistent agent or Device Profiler methods. This is the information that FortiNAC uses to compare against the Whitelisted SSID/AP group.
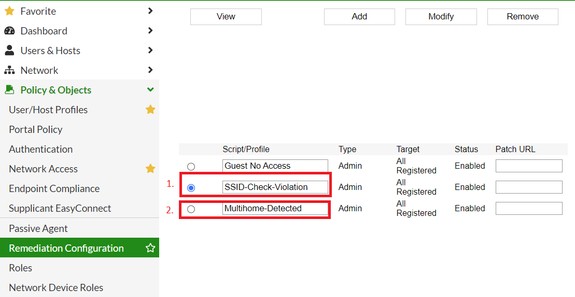
If the SSID/AP where they are connected is not part of this group an event 'Adapter connected to a disallowed SSID' will be generated and an alarm created. This alarm sets a failure for a pre-created 'SSID-Check-Violation' admin scan and marks the host at risk.
When the host is marked at risk FortiNAC applies State-based control which will remediate the host irrelevant of the Network access policy they match.
To validate and check the admin scans go to Policy&Objects -> Remediation Configuration.
The purpose of admin scans is to mark hosts at risk when they fail a scan and present to them a specific page informing users of remediation actions. The portal page is defined within the Admin scan.
In such cases when a connection is detected to a disallowed SSID the Host will be marked at risk.
Disconnecting from that SSID and re-validation of the compliance policy will mark the host 'Safe' again.
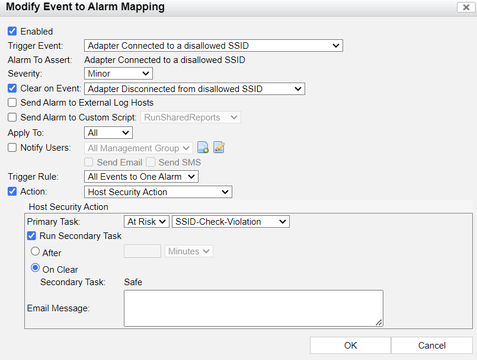
The alarm mapping to the Trigger Event 'Adapter Connected to a Disallowed SSID' can be modified in Logs -> Event&Alarms -> Mappings.
Administrators can modify the settings depending on need or add additional tasks to be performed after the Primary one.
- Detect Multihoming.
This feature will detect multiple-connected adapters and generate a 'Multihomed Host Detected' event and Alarm.
If the host has an online wired adapter and the user connects additionally to wireless they will be detected and marked at risk.
The alarm actions are by default configured to mark at risk for a 'Multihome-Detected' admin scan. The host will need to have only one connection (online adapter) in order to be marked Safe and get production access through Network Access policies.
The 'Multihomed Host Detected' event to alarm mapping can be edited the same as in previous example in Logs -> Event&Alarms -> Mappings.
Related document:
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.