- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: Authentication, Remote server group...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 04-17-2015 02:35 AM Edited on 06-09-2022 02:48 PM By Anonymous
Description
The purpose of this article is to clarify the usage of a specific string for in group matching, which can be set in firewall user group. By default, no attribute is checked, anything is accepted.
Solution
For RADIUS based user groups.
This is pure string comparison between what is in the 'set group-name' inside the FortiGate user group configuration and what the FortiGate gets in Access-Accept response to user authentication from the RADIUS server.
In Access-Accept the FortiGate looks for RADIUS AVP Fortinet-Group-Name.
The RADIUS server has to have the Fortinet dictionary loaded (most of the common servers does, otherwise see 'Resources' for link to it) and user need to have set AVP Fortinet-Group-Name to some string which we will use in comparison, for example 'GRP-one'.
Note that some RADIUS servers like FortiAuthenticator can provide RADIUS attributes on per user or per group basis.
So, either every single user has its own AVP, or user is group member and when authentication happens then the user inherits AVP from the group.
The name of the user group on RADIUS server (like in this inherit case) has no direct connection to AVP, so simply by choosing the group is not enough.
If using such group (GROUP-RAD in examples) for authentication, then when the user tries to log in, then fnbamd daemon on FortiGate will be involved, create authentication session and send out RADIUS Access-Request with provided user credentials.
And if username and password match on RADIUS server then server should respond Access-Accept with AVP Fortinet-Group-Name inside.
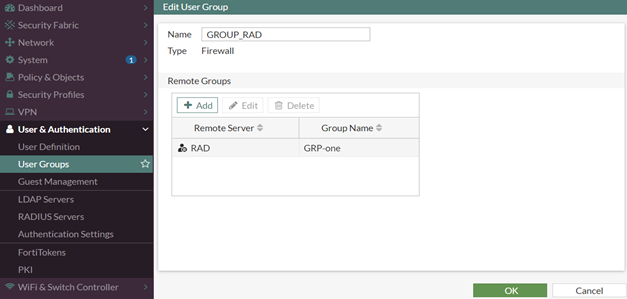
And if returned AVP reads as 'GRP-one' string, then the user will be seen as matching firewall user group 'GROUP_RAD'.
All the users on RADIUS which will have Fortinet-Group-Name = 'GRP-one' will possibly match as members of 'GROUP_RAD'.
FortiGate CLI.
# config user radius
edit "RAD"
set server "10.0.0.1"
set secret fortinet
next
end
# config user group
edit "GROUP_RAD"
set member "RAD"
# config match
edit 1
set server-name "RAD"
set group-name "GRP-one"
next
end
next
end
- stored in /etc/raddb/users.
- shown user name 'grptest1'.
grptest1 Cleartext-Password := "Fortinet2021!"
User-Service-Type = Login-User,
Fortinet-Group-Name = "GRP-one"
Verification and troubleshooting.
1) FortiGate-Lab # diagnose test authserver radius RAD pap grptest1 Fortinet2021!
authenticate 'grptest1' against 'pap' succeeded, server=primary assigned_rad_session_id=1198986977 session_timeout=0 secs idle_timeout=0 secs!
Group membership(s) - GRP-one
2) Extended with debug.
FortiGate-Lab # diag debug application fnbamd 73) Packet capture from GUI or via diag sniffer packet.
FortiGate-Lab # diag debug enable
FortiGate-Lab # diagnose test authserver radius RAD pap grptest1 Fortinet2021!
handle_req-Rcvd auth req 1198986978 for grptest1 in RAD opt=0000001d prot=0
fnbamd_pop3_start-grptest1
fnbamd_cfg_get_radius_list_by_server-Loading RADIUS server 'RAD'
fnbamd_create_radius_socket-Opened radius socket 15
fnbamd_create_radius_socket-Opened radius socket 16
fnbamd_radius_auth_send-Compose RADIUS request
fnbamd_rad_dns_cb-10.0.0.1->10.0.0.1
fnbamd_rad_send-Sent radius req to server 'RAD': fd=15, IP=10.0.0.1(10.0.0.1:1812) code=1 id=23 len=100 user="grptest1" using PAP
create_auth_session-Total 1 server(s) to try
fnbamd_radius_auth_validate_pkt-RADIUS resp code 2
fnbamd_auth_handle_radius_result-->Result for radius svr 'RAD' 10.0.0.1(1) is 0
fnbamd_radius_group_match-Skipping group matching
find_matched_usr_grps-Skipped group matching
fnbamd_comm_send_result-Sending result 0 (nid 0) for req 1198986978, len=2049
authenticate 'grptest1' against 'pap' succeeded, server=primary assigned_rad_session_id=1198986978 session_timeout=0 secs idle_timeout=0 secs!
Group membership(s) - GRP-one
FortiGate-Lab # diag sniffer packet any 'port 1812' 6 0 a
Note.
The group matching is not set per default, any string will be accepted. If this is the intention, DO NOT change it.
Be careful not to use the literal string 'Any' for matching.In this case the FortiGate will try to match the AVP Fortinet-Group-Name to a string 'Any'.This will lead to authentication failures unless the value for the Fortinet-Group-Name is the literal string 'Any'.This can lead to confusion as this cannot be visually spotted in the group overview.
From CLI.
# config user groupEither the string can be removed from the FortiGate GUI by editing the user group remote matching or via CLI by removing/changing the match.
edit "GROUP_RAD"
set member "RAD"
# config match
edit 1
set server-name "RAD"
set group-name "Any" <----- Instruction to match against the literal string 'Any'.
next
end
next
end
# config user groupIn this example the group configuration should then look like:
edit "GROUP_RAD"
set member "RAD"
# config match
delete 1
end
next
end
# Config user group
edit "GROUP_RAD"
set member "RAD"
next
end
Related Articles
Technical Tip: FortiGate Radius VSA Dictionary (vendor-specific attributes)
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.