- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: How to avoid certificate error mess...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on
01-24-2018
05:39 AM
Edited on
04-04-2023
06:31 AM
By
![]() Anthony_E
Anthony_E
Purpose
While using third party certificates signed by intermediate CA/ root CA, sometimes FortiOS will not send the complete certificate chain to the client. This occurs due to an incorrect configuration and gives a certificate error message on the client browser.
This article helps to avoid such error messages.
Expectations, Requirements
This article is applicable for the following authentication types:
1. Admin WebUI login to FortiGate
2. SSL VPN authentication to FortiGate
3. Captive Portal authentication over HTTPS to FortiGate
This article is applicable for the following certificate types:
1. Locally signed certificates
2. Certificates signed by well-known CAs.
Configuration
1. While authenticating against captive portal of a FortiGate, a certificate error message is sometimes displayed. The certificate error can be caused due to several Alert messages as described in the TLS/SSL RFCs. Viewing the developer tools available in the web browser, helps narrow down the exact root cause for the certificate error message.
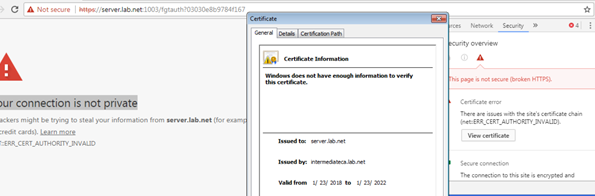
2. In this case the certificate error message was caused due to an invalid/no chain of certificate verifying the authenticity of the server certificate provided in the SSL/TLS handshake.
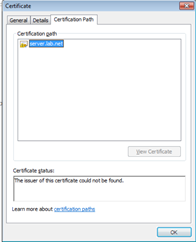
The certificate chain is missing as shown in the certification path tab
3. Using WireShark, the same can be verified by capturing the SSL/TLS handshake between the browser and the server
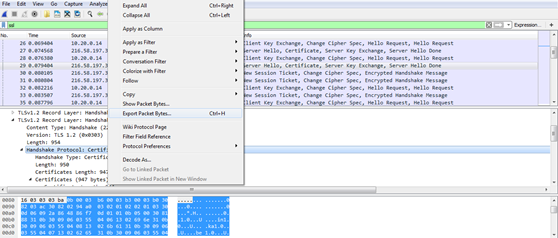
4. Click on Export Packet Bytes and save the file as certificate.cer and open the certificate.cer which looks like below.
5. Now go to the FortiGate GUI and upload the public key/certificate of Root CA and Intermediate CA in the CA Certificate section in pem/cer format.
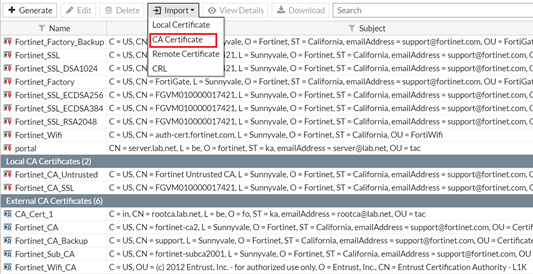
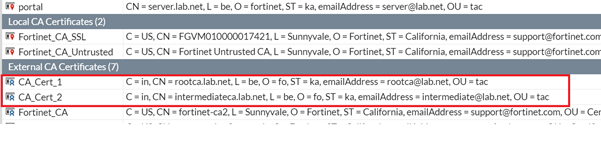
6. Make sure that you have the Root CA and Intermediate CA under the External CA certificates
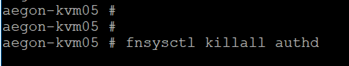
7. Restart the authd process
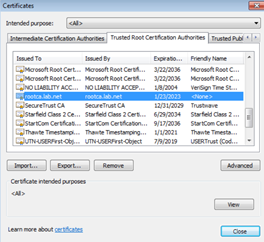
8. On the browser, ensure that the Root CA is present/installed/trusted. Intermediate CA doesn't need to be installed on the browser because the intermediate CA will be sent in the SSL/TLS handshake by the FortiGate.
9. Re-open the browser and access any web page. This redirects to the captive portal login page on the FortiGate.

10. The certificate chain is present this time and no error is seen on the browser.
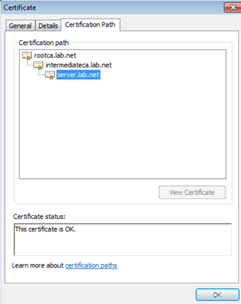
10. Verify using Wireshark to capture the SSL/TLS Handshake.

11. Points to Note
a. Public key of the Root and Intermediate CA needs to be uploaded to FortiGate, as Remote CA certs.
b. The following two CLI commands are in place.

See also : Preventing certificate warnings CookBook
Related Articles
Technical Note: Certificate warning when connecting to SSLVPN from Linux devices
Technical Note: SSL inspection on multiple FortiGates using the same certificate (OpenSSL method)
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.